Introduction
In the year 2017, a certain version of internet-connected programmers, manufactured by a global medical device company, were found to have serious cybersecurity issues.
These programmers, portable computer devices, were used by medical professionals to program and manage implantable cardiac devices.
The devices when connected to internet, were susceptible to unauthorized access by hackers who could manipulate the programmer’s functionality. This lead to the recall of these device, affecting nearly 30,000 units.
Reports suggested that this loop-hole existed due to the lack of robust network security measures.
This and several such similar incidents are crude reminder of the fact that in this IoT (Internet of Things) Universe, Data/Network/Device Security should be the top priority of all the stakeholders.
The Why and What of Security of Internet of Things (IoT) Systems
The foundation of the IoT (Internet of Things) technology stack is supported by connectivity protocols (MQTT, Wi-Fi, Ethernet and more).
In such interconnected networks, any unsecured device or a connectivity port can act an entry point for the hackers.
The consequences of such an IoT security breach can be detrimental for the business, for the consumers as well as for the industry .
Now in order to be able to design a secure Internet of Things (IoT) system, as a product developer/organization/IoT enthusiast, it is important to develop an understanding and realization regarding the following:
- What are the pre-requisites for designing a fail-proof and efficient IoT security strategy?
- What are the challenges involved in designing an IoT security framework?
This blog is our quest to help you develop this understanding

Designing an Ideal IoT Security Framework:
In its simplest form, architecture of every IoT application includes the following three main components:
- The Devices/IoT Sensors (Data Aggregation)
- IoT Gateway (Data Transmission)
- Network and Cloud (data is stored and processed)
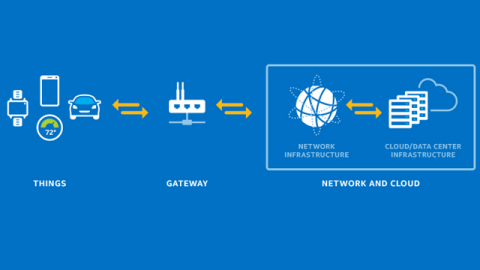
Image 2: IoT architecture. Image Source: Intel
A robust and fail-proof IoT security strategy should be designed with the aim of implementing security at all the above levels.
So what are the security techniques that must be central to such a multi-level IoT security strategy? Let us explore!
Device Security:
Some of the best security practices when it comes to IoT devices include:
Microcontroller/Microprocessor UIDs – Every IoT device is powered either by a microcontroller or a microprocessor. Since these Microcontrollers perform several critical functions and are accessible-via the network, they should be absolutely protected.
To prevent them (Microcontroller) from any unauthorized access, they are assigned specific unique identification (UIDs) keys. UIDs are often hard coded into the microcontroller platforms by the chip vendors.
These UIDs help in uniquely identifying the microcontrollers and can be leveraged to deny unauthorized access or data duplication.
That’s why several manufacturers design their chips with unique identification (UIDs) keys these days. These UIDs make sure an extra layer of security is added to the IoT data collection points or devices and the first step of the chain is safe.
Root of Trust – “Trust” in IoT security refers to an expectation that an IoT device is operating as designed. Software trusts that hardware is operating as it should be. Applications trust that the operating system is not corrupting files. This process of maintaining trust between devices is called authentication. An IoT device’s root of trust is the point where authentication starts and then extends through each layer.
A part of trust computing module, root of trust defines set of functions / software codes, which are hardened into a hardware module like Hardware Security Module (HSM).
A root of Trust offers the following security features:
- Check unauthorized access of data encrypted on hard drive
- Detect and report any suspicious/unauthorized changes to the system programs
- Memory curtaining to prevent programs against unauthorized reading or reprogramming onto each other’s memory
Establishing the root of trust in an IoT system means ensuring that the hardware is working as it is expected to work, that the firmware is unbroken. This includes ensuring that the:
- software ported in the microcontroller cannot be modified once written into the memory
- Microcontrollers boots only from a trusted boot
Physical Security – In addition to the above security mechanisms, developers can take the following measures to curb hacking:
- In many a situations, your IoT application may include unused ports, communication stacks that can act as a entry point into the application for potential hackers. Hence, prior to the deployment of the IoT application, any such unused ports should be disabled.
- Devices (microcontrollers FPGAs) and product designs are required to undergo a post-production testing and verification. This is done using a standard interface called Joint Test Action Group a.k.a JTAG.JTAG interfaces can be used for:
- Reading and writing from memory
- Accessing , managing / reprogramming firmware
- Accessing Private instructions for data encoding etc.
Hackers keep an eye on active (open) JTAGS to intrude into the embedded systems. The best way to prevent this is to lock or disable the JTAG in your field devices prior to deployment.
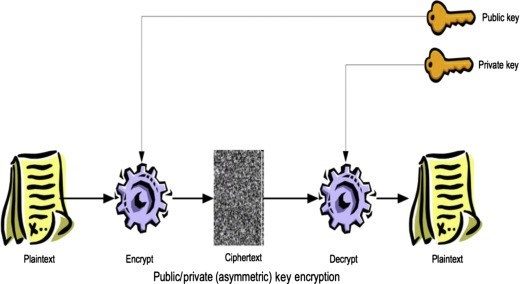
- Standard private and public encryption key mechanism: This calls for standard Public-key cryptography solutions to encrypt and decrypt data, using a set of private and/or public keys.Public key encryption algorithm is one of the important methods of ensuring security in modern applications and protocols. This supports data confidentiality, authenticity and integrity.

Image 3: Public key encryption; Image Source: ScienceDirect
IoT Gateway Security:
The security practices discussed for devices are also applicable to gateways, in addition to the following:
Blacklisting/Whitelisting Mac addresses – In IoT, blacklisting is a basic access control mechanism that allows everyone access, except to those included in the black list.
This is implemented by keeping an inventory of wireless clients, based on the MAC address, who are denied access to the IoT network.
Alternatively there is a whitelist, which is an inventory of MAC addresses that are allowed access.By specifying exactly who can access the gateway and who cannot, a tight security layer can be enforced within an IoT system.
An important point to remember while doing this is that blacklisting / whitelisting needs to be configured at the code development stage. It cannot be done after production.
Magic Number Sharing – This mechanism is typical of headless devices (devices that don’t have a display).
In such devices, magic number is implemented as a security practice. This is a unique number which is shared only with validated users. It is hard coded into the program and anyone with the wrong magic number is restricted from logging into the system.
Cloud and Network Security
Since all the data collected and transmitted over the IoT gateway reaches the cloud for storage and processing, securing this phase is ultra crucial.
Some techniques which can be used include:
User access management of cloud data – It needs to be ensured that all the data is physically secure. For this, both the IoT gateway device and the cloud should have SSL certificates installed.
For additional security, organizations implement SSL certificates along with 128 bit encryption key combinations.
For a detailed insight about Embitel’s multi-level IoT security practices, read our FAQ document
Securing cloud API – The cloud being the central repository of your enterprise data, you must keep your Cloud API endpoints secure. One of the most popular methods to secure Cloud data API calls is Access Token mechanisms .
Access tokens are specific credentials that identify that the application bearing the token is authorized to access the cloud API and is has the permission to execute a predetermined set of actions, defined within the scope granted.
Whenever an application has to access the cloud API, it has to specify the assigned Access token in HTTP Authorization header, while sending request to the cloud.
Another way is to use API keys to monitor the API calls made to access the cloud data.
This helps in determining and fixing the number of safe connection requests. These are also useful during the production phase, as one can monitor how frequently an API call is generated. This becomes important in order to keep a upper cap on the number of API calls that can be invoked during product development.Security of data at rest – Technically speaking , any digital data is defined to exit in one of the following three states:
- Data in use- which is the active data,
- Data in Transit- information that flows over a network
- Data at rest- inactive data or data that is stored physically in any digital form – cloud database, archives ,datawarehoueses etc.
A data at rest will often have a logical structure ( location, connection with other data points), as it is stored in the database.
This makes it vulnerable to unauthorized access ( outside the network) and data duplication and manipulation. Thus, data at rest is a cause of security concern for businesses and organizations.
Often data at rest is primarily protected by conventional perimeter-based defensive techniques mechanisms such as firewalls and anti-virus programs.
However, these barriers are vulnerable. Business organizations need additional layers of defense to protect sensitive enterprise data from intruders.
Encryption is one of the best ways to ensure the security of data at rest. Veracrypt is one of the widely used software solution for encrypting a data at rest.
Veracrypt is an open source software for disk encryption and decryption. It keeps the data encrypted at rest and decrypts the data only when it is required. Veracrypt allows the encrypted data to be read/edited only with a valid password.
Challenges Ahead
It is imperative to develop an IoT security strategy along with your IoT business model to protect your critical assets and data.
But before setting out to design a IoT security strategy solution for your business, it is also advisable to keep a check on some challenges, that you may face .
We are listing down few of the challenges that are unique to IoT ecosystem, that you may consider:
- No One-Size Fits-all Solution : It is difficult to develop a generic “one size fits all” IoT security strategy or model.An IoT ecosystem is heterogenous in nature: It includes communication protocols, architectures, services, use-cases standards and device capabilities that are much wider, and varied.
- New Use-cases and security challenges. Increased automation and digitization of business, powered by IoT has paved way for new security concerns.Newer uses cases of automation often involve usage of newer and innovative technology architectures, hardware and software components- with limited or immature security capabilities
In such scenarios, ensure that your choice of technology and architecture is able to address security concerns related to:
- Data confidentiality,
- Privacy and
- Trust
- Balancing the Security vs Cost Proposition: As a best practice, using high performance processors and hardware components with in-built security mechanisms ( Root of Trust, TPM, Public Key Infrastructure) is the most robust path for security. But this comes at added cost.
- When it comes to security breach, there is a constant debate among the industry stakeholders as to who will take the responsibility- the chip vendors , or the service providers?It is advisable to be develop clarity about the responsibilities and ownership, in an event of security breach. This makes it easy to formulate a solution and address the security challenge at the earliest.
Conclusion
There is no substitute for security in a highly-connected, data-intensive and fast-growing IoT ecosystem. Data being a chief component of today’s business success and competitive strategy, security should be the core of your IoT solution.