About the Customer:
A leading Tier-1 automotive supplier was developing a new generation of vehicle control modules for a premium OEM. These modules included a central SoC and an I/O Controller (IOC) to control essential in-vehicle functions. Communication channel used was UART.
The challenge was to ensure that only authorized hardware could communicate with the control systems.
Business Challenges:
The customer had one clear mandate from the OEM: Prevent unauthorized hardware from issuing commands to the IOC.
If the UART interface was compromised, an attacker could:
- Inject unauthorized commands directly to the IOC
- Replay previously recorded messages
- Illegitimately enable premium vehicle features
Initially, this security was enforced by a Trusted Application (TA) developed by another vendor.
But when the vendor withdrew support, the customer lost their trusted mechanism to validate hardware authenticity.
To make matters more challenging:
- The SoC did not include a Hardware Security Module (HSM)
- Without an HSM, several critical questions emerged:
- Where do you safely store cryptographic secrets?
- How do you verify whether a connected module is OEM-approved?
- How can you ensure messages aren’t spoofed, tampered with, or replayed?
The solution was to develop a robust trusted application that could secure any such tampering and security breach.
Embitel’s Solution:
The specialized arm (Trusted Application Development) of our automotive cybersecurity team at diconium Germany stepped in with a solution centred around the Trusted Execution Environment (TEE) available on the SoC, Kinibi.
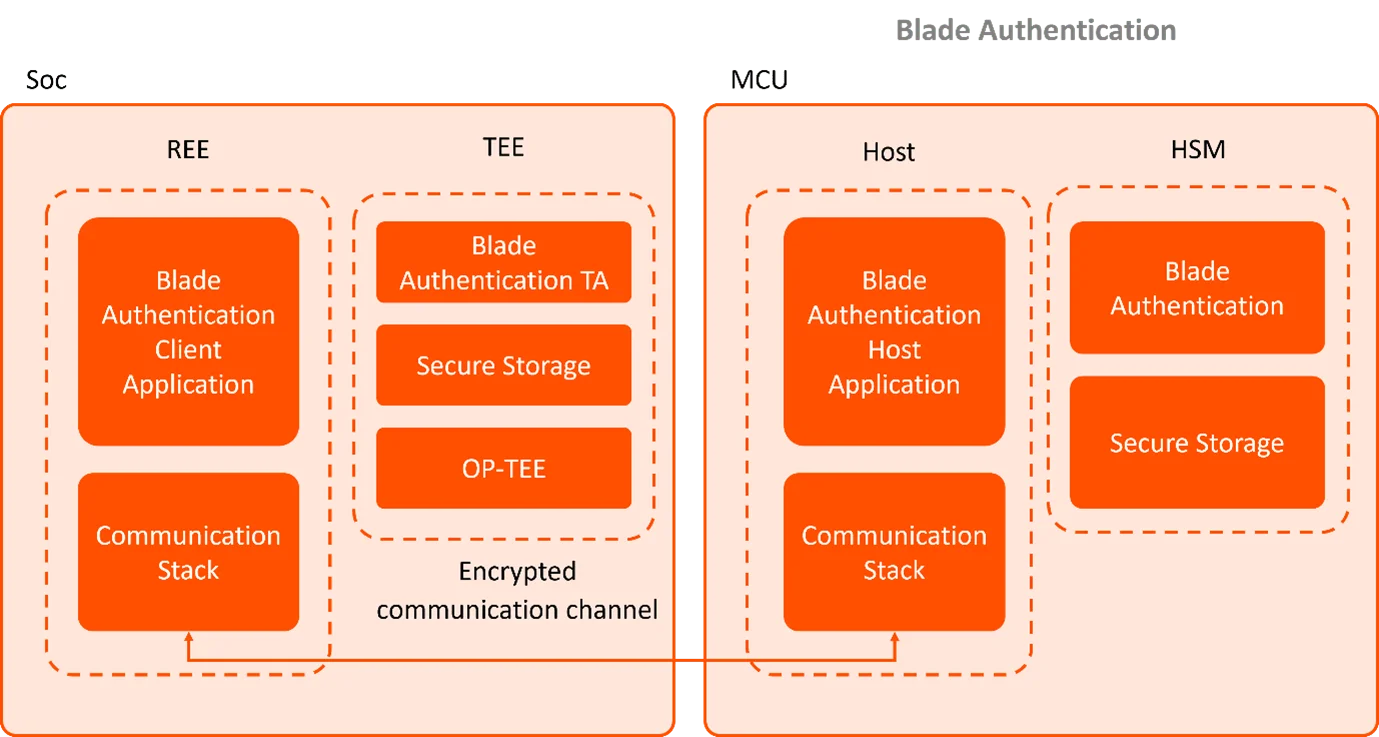
A new Trusted Application (TA) was developed to:
- Secure the Communication Channel
- Protect confidential data Inside TEE
- Authenticate Messages
- Restrict Access to Approved Hardware Only
A 3-step handshake (Request → Response → Confirmation) was implemented to establish a secure session between the SoC and IOC. Each side had a pre-shared key burned in during manufacturing.
The TA ensured this key was never exposed to the OS or stored in memory in plaintext. All cryptographic operations and validations were done inside the TEE, isolated from potential attackers with access to the normal OS.
Session keys were generated post-handshake. Each command included random numbers and counters to prevent message replay and spoofing.
The TA denied communication unless the incoming device could prove that it contained correct shared key, validating that it was an OEM-approved hardware.
Embitel Impact:
The solution eliminated the risk of unauthorized command injection and feature unlocking via hardware tampering.
With the specialized trusted application in place, the customer could confidently launch their product without worrying about cybersecurity threats. The TA acted as a gatekeeper ensuring that only authenticated, verified hardware could access or modify sensitive ECU functions.
Tools and Technologies:
- Kinibi TEE on production hardware
- OP-TEE + QEMU for CI testing
- C / C++ for TA and wrapper libraries
- GlobalPlatform APIs for standardized TA structure


