Speed to Market
Rapid development and deployment of Trusted Applications, ensuring quicker delivery of secure embedded solutions.






A Trusted Application (TA) is a secure software component that runs within a Trusted Execution Environment (TEE). It ensures isolation and protection for cryptographic processing, secure storage, and access control.
SoCs powering ADAS, telematics solutions, and Infotainment system face persistent cybersecurity threats. Protecting sensitive memory segments and cryptographic keys is crucial to prevent unauthorized access and modifications, ensuring automotive system security.
Trusted Execution Environment (TEE) along with Trusted Applications act as isolated enclave to shield all operations involving sensitive data.
In modern automotive ECUs, a Trusted Application like the Secure OTA Firmware Update Manager ensures system integrity. It decrypts and validates firmware updates by verifying digital signatures and certificate chains. Rollback protection blocks outdated or vulnerable versions, keeping the vehicle secure and reliable.
Our cybersecurity teams in Germany and India develop such Trusted Applications (TAs) that isolate critical operations, safeguard sensitive data, and enforce strict access controls. These TAs are tailored for diverse platforms, including automotive ECUs, industrial IoT gateways, healthcare devices, consumer electronics, and EV charging systems. Some of the common trusted applications include Cryptographic Key Management, Data Encryption, Secure OTA update etc.
Our Trusted Applications address critical challenges for customers requiring secure access, data protection, and cryptographic functionality. The TAs are built for Trusted Execution Environments (TEEs) to tackle critical cybersecurity needs. They secure access to sensitive hardware, protect data from tampering, and handle cryptographic operations without exposing keys.

Some SoC peripherals, like OTP memory, are only accessible through the TEE. Our TAs enable secure access to manage unique IDs and anti-rollback counters.

Cryptographic operations such as signing, encryption, and decryption often expose keys. Our TAs perform these securely within the TEE, ensuring keys remain protected.

Critical data like certificate hashes or root keys need to be tamper-proof. Our TAs securely store this information to guarantee its integrity for validation processes.

Some data, like anti-rollback counters, must only change under strict rules. Our TAs ensure updates are controlled, preventing unauthorized downgrades or vulnerabilities.
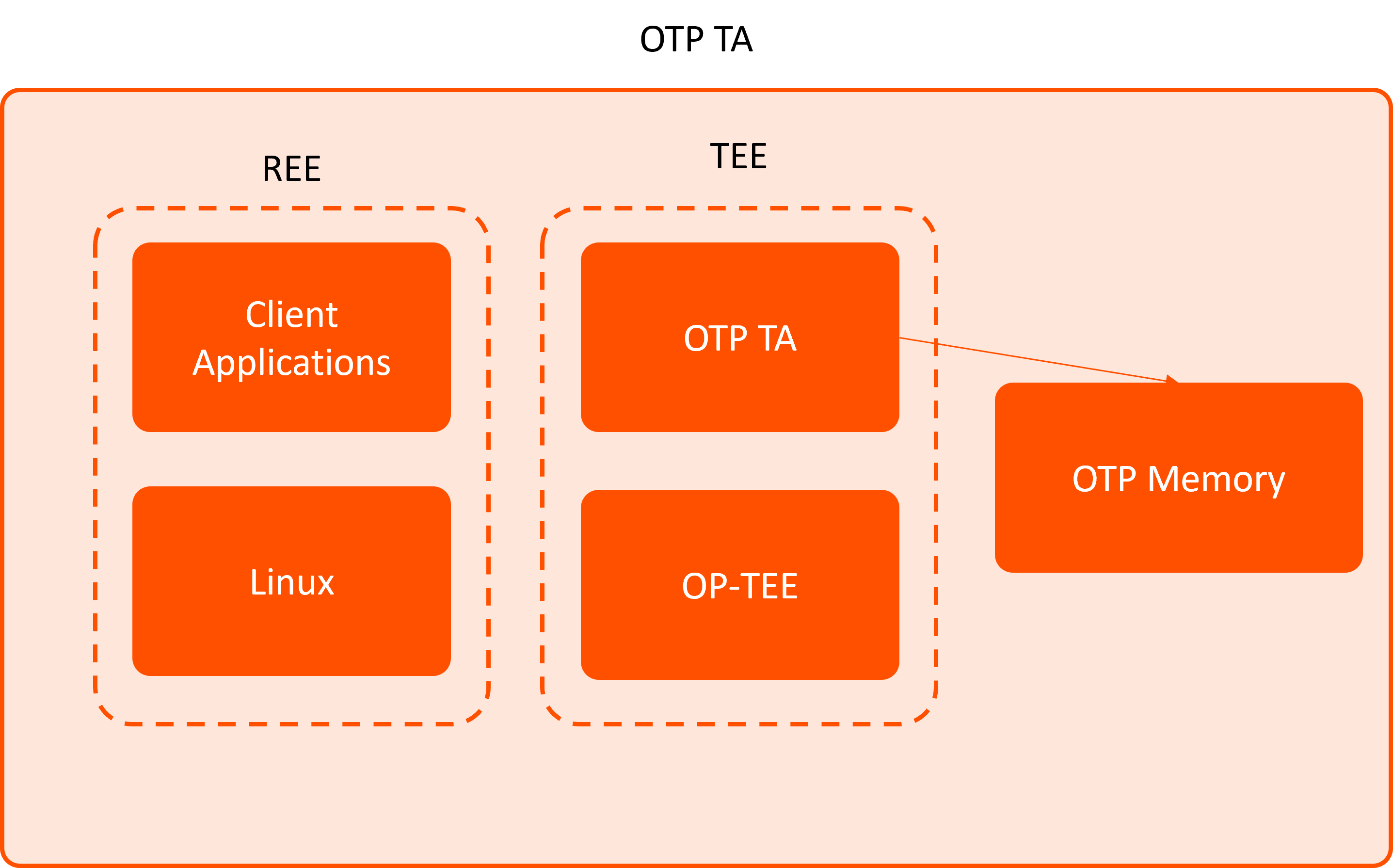
We developed a TA that provided both hard OTP and soft OTP functionality.
This allowed the client to store immutable data securely, ensuring that keys and other sensitive information remain confidential and protected from unauthorized access.
All tests were conducted using OP-TEE to ensure compatibility and performance.
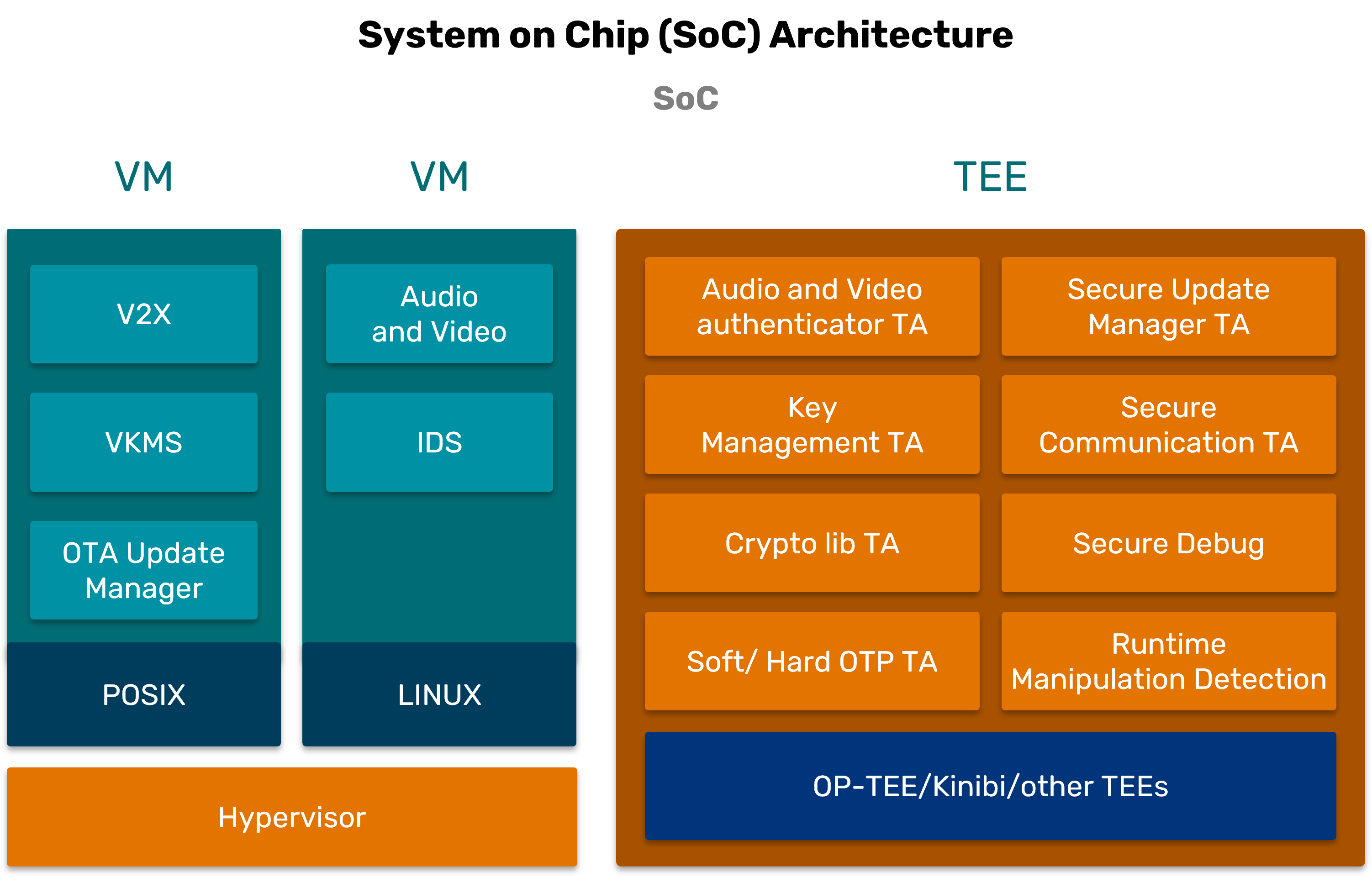
We developed a Trusted Application for standard cryptographic functions—encryption, decryption, signature verification, and authentication—tested using OP-TEE. These functions serve as the foundation building blocks for various secure use cases.
We developed a decryption module and integrity validator for the software update manager, enabling secure decryption and verification of update packages before installation.
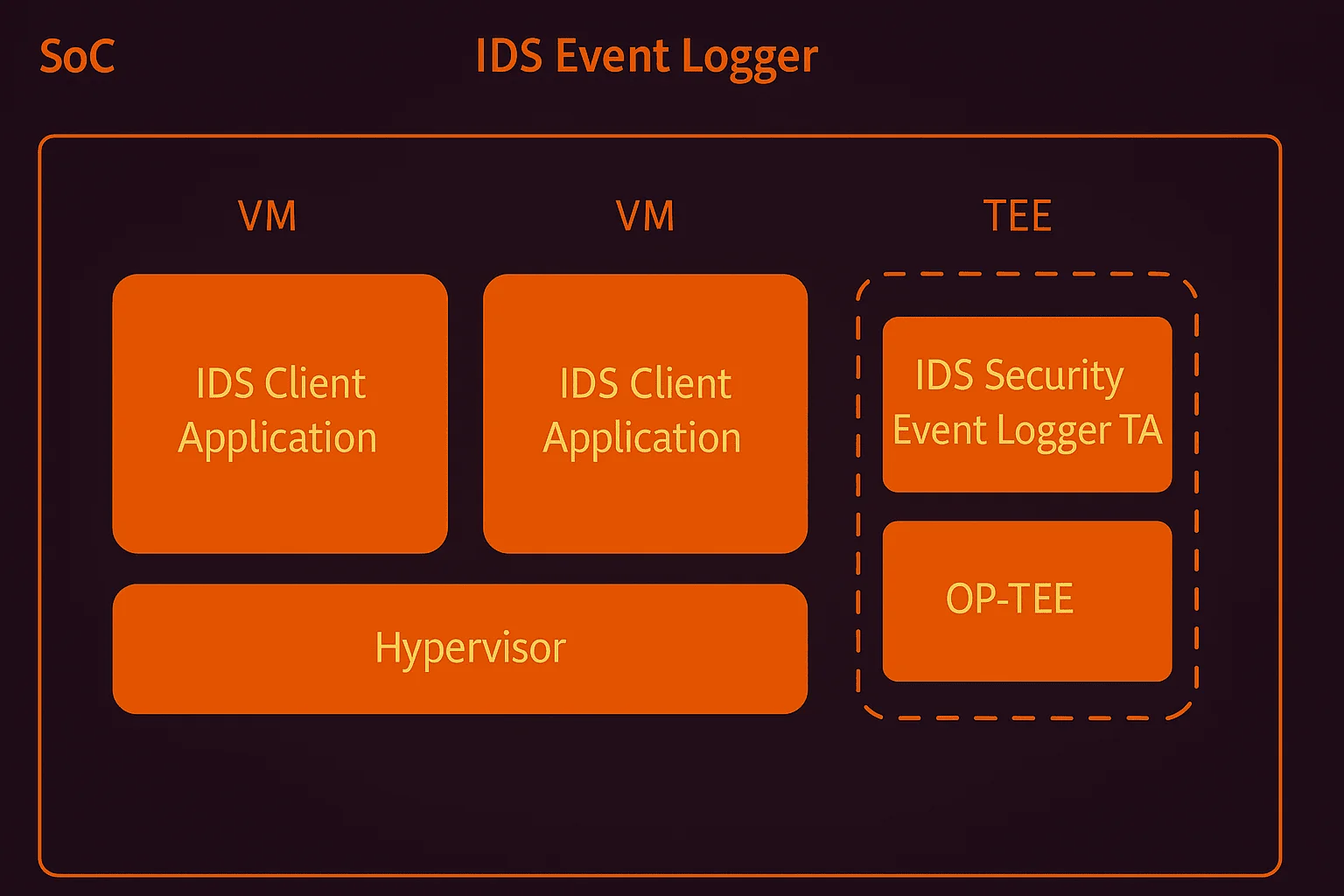
A client needed an IDS event logging solution that allowed multiple VMs to access logs securely, while maintaining strict read/write controls.
We developed a Trusted Application to handle event logging. This TA implemented controlled access permissions, ensuring only authorized VMs could read or write to the logs. OP-TEE was used for testing, ensuring the implementation met the client’s security requirements.
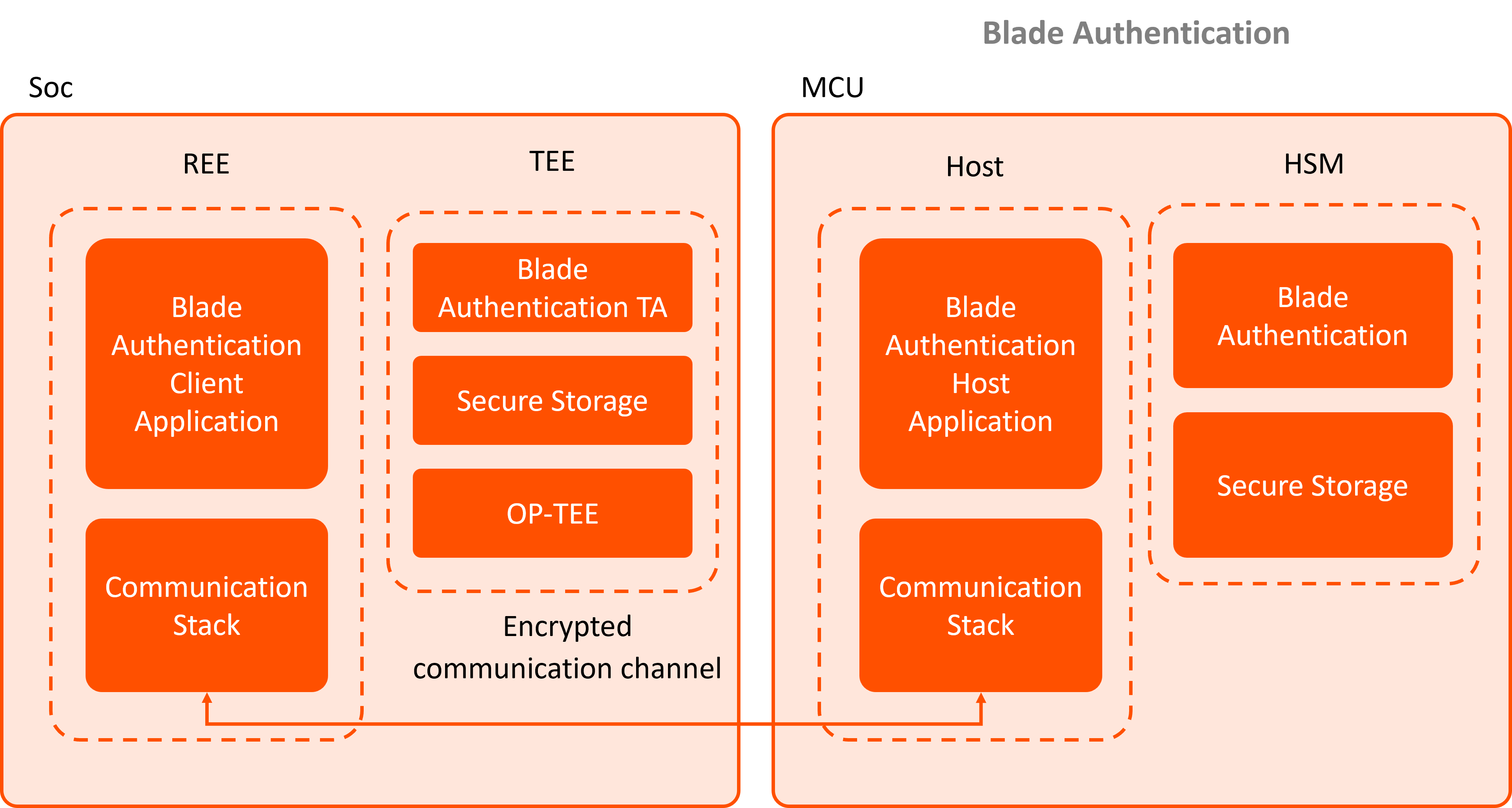
Our team developed trusted application that ensured mutual authentication between components, enabling session key generation and encrypted communication over a trusted channel. Testing on OP-TEE confirmed the TA’s reliability and security.
Custom Trusted Applications to meet unique requirements, including anti-rollback protection, secure logging, and performance-driven compliance.
Development of secure TAs for both production hardware and virtual environments, leveraging Kinibi, QEMU, and OP-TEE.
End-to-end encryption, decryption, and key management solutions, secure signing etc. integrated with industry-leading cryptographic libraries such as OpenSSL.
Implementation of standardized APIs for secure communication, cryptographic operations, and custom libraries to wrap TA functionality for seamless Linux integration.

Compliant with ASPICE, ISO 21434, and other industry standards, providing robust, dependable results.

Reusable components and best-cost country development practices lower project costs.

Clean, modular APIs that integrate smoothly with Linux, QNX, Autosar, and other rich OS environments.

Fast response times for vulnerabilities, bug fixes, and ongoing system improvements.

Most TAs are implemented in C due to their low-level control and efficiency. Secure coding practices are crucial, as vulnerabilities in TA code could expose sensitive data. Some platforms provide specific SDKs or development frameworks that include libraries, headers, and tools to streamline TA development.
| Automotive Security | Media & Digital Rights Management | Device & Virtualized System Security | Firmware & Over-the-Air (OTA) Protection | Data Protection & Cryptography |
|---|---|---|---|---|
|
|
|
|
|
A TEE is a secure area within a device's main processor that isolates sensitive operations and data from the rest of the system.
It’s critical for protecting cryptographic keys, securing boot processes, and ensuring safe firmware updates, especially in automotive and IoT devices.
Yes, TAs are highly customizable to meet specific hardware requirements and industry needs. They can integrate with SoC peripherals like OTP memory and secure cryptographic operations. They can adapt to unique use cases like anti-rollback counters or certificate validation.
We have extensive experience developing TAs for Kinibi, OP-TEE, and other widely used TEEs. Our expertise covers a range of hardware platforms, including automotive-grade ECUs, IoT gateways, consumer electronics processors, and specialized industrial controllers.
By leveraging our understanding of both real hardware environments (Kinibi) and virtualized development platforms (Qemu), we provide flexible solutions tailored to your specific hardware ecosystem.
TAs run within the TEE to handle sensitive operations like encryption, data storage, and access control. They ensure critical data and keys are never exposed to the untrusted environment, protecting systems from unauthorized access and cyber threats.
Trusted Applications (TAs) operate within the Trusted Execution Environment (TEE), an isolated and secure area of the processor. When performing cryptographic operations like signing, encryption, and decryption, TAs ensure that sensitive keys never leave the TEE.
Here’s how they ensure security:
This approach ensures the integrity and confidentiality of cryptographic processes, making TAs an essential component for secure systems.
Yes, we specialize in custom TA development to meet unique requirements. Whether you need a TA for anti-rollback protection, secure event logging, runtime integrity checks, or digital rights management (DRM), we can design, implement, and integrate a solution that addresses your exact needs.
Our development process involves close collaboration to ensure that the TA aligns with your technical specifications, industry regulations, and performance expectations.