About the Customer:
Our customer is an automotive tier-1 specializing in innovative solutions around mechatronics of automobiles. Some of the leading OEMs around the globe trust them for their sophisticated solutions.
As the industry is fast embracing automotive cybersecurity, our customer has been one of the earliest adopters of cybersecurity standards and practices. Partnering with us takes their commitment to automotive cybersecurity to newer heights.
Business Challenges:
The primary challenge for our customer was to develop a secure bootloader that could flash/reprogram the ECU (control unit). There was a certain level of cybersecurity required for the ECU that entailed numerous security implementations including digital signature.
Here’s a snapshot of the major challenges that needed to be addressed:
- The ECU comprised 2 microcontrollers that required a 1-wire gateway
- Both CAN and LIN based bootloader was required as ECU had both CAN and LIN variant.
- The Hardware Security Module provided by Microchip required drivers to be developed
- Secure Bootloader was needed to be developed with advanced cybersecurity features as per ISO 21434 standard
Since the customer needed a faster time-to-market for their solution, they partnered with us for bootloader development and other solutions. We have a proven track record of delivering secure bootloaders for automotive ECUs.
Embitel’s Solution:
Our automotive team was primarily tasked with the development of a secure bootloader that would interact with the Hardware Security Module (HSM) of the ECU and ensure secure ECU flashing. In the process, the image(.hex/.srec) file and the digital signature will be validated with the HSM.
Additionally, the project scope also included developing a ‘gateway’ to facilitate flashing of 2 microcontrollers. Since the ECU had two variants- CAN and LIN, we had to develop bootloaders for both networks.
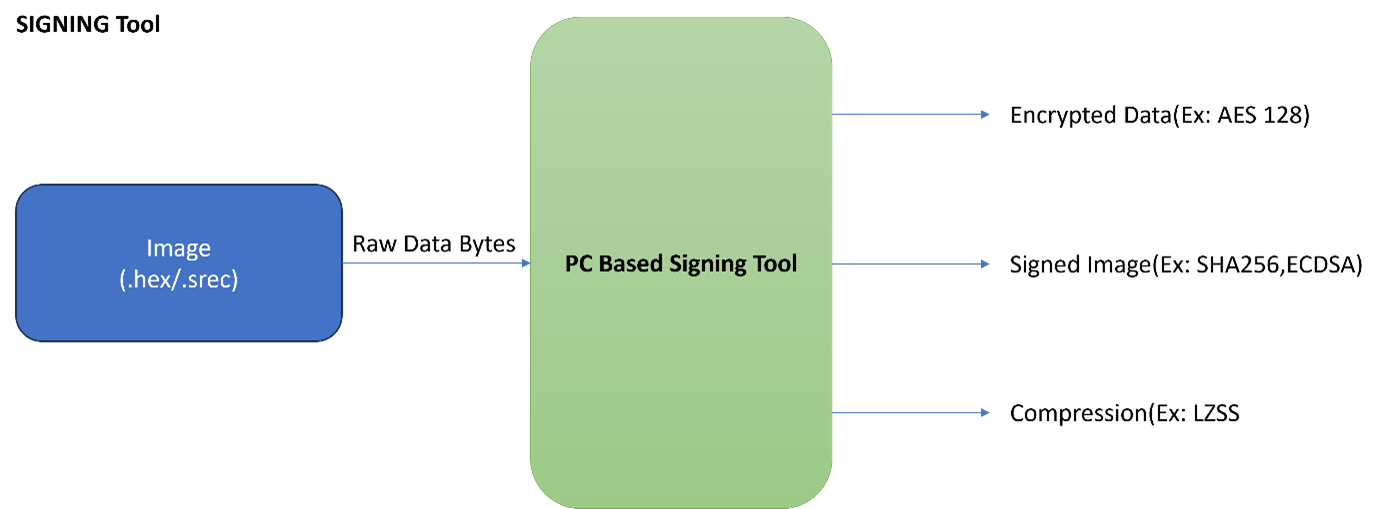
To facilitate secure ECU flashing, our customer requested us to develop a signing tool that would encrypt the image (.hex/.srec) file based on algorithms required by the customer.
The team started to work parallelly on these three applications.
Details of the solutions built for the customer:
- Secure Bootloader: The secure bootloader comprises of algorithms such as AES- 128, Elliptical Curve Digital Signature algorithm (ECDSA), CRC-32 integrity and data authenticity mechanism. We developed the secure bootloader for both CAN and LIN protocols as requested by the customer.
- Low-level drivers required by the microcontroller: Device drivers such as HSM drivers and all other low-level drivers needed by the microcontrollers such as NVM handler, CAN, LIN drivers were developed.
- 1-wire Gateway: The data coming for microcontroller 2 has to be forwarded from microcontroller 1. We developed a secure gateway for that purpose. It is a UART based 1-wire gateway solely for transmitting data from one MCU to another.
Gateway proved to be a critical piece of solution to build especially in a 2 MCU environment. The gateway must ensure that the number of bytes of data sent to MCU 2 is received without any loss. Also, the data sent to MCU 2 through the gateway must be validated through HSM. Hence, reliability is the key here. We tested the communication rigorously to rule out any discrepancies.
- Signing Tool: We developed the signing tool to solve the problem of encrypting the firmware image file based on secure algorithms of choice. The signing tool accepts .hex or .srec application images, then encrypts and compresses them using algorithms customizable to meet your specific requirements. Finally, it generates a robust signature for the image, ensuring the integrity and authenticity of your software with an algorithm shaped by your unique needs.
Other Deliverables provided to the customer:
- The secure bootloader developed for the customer was based on CAN and LIN. Hence we delivered our ready-to-integrate CAN protocol (CAN interface layer and network management layer) and LIN protocol (LIN interface layer, network management layer and node service).
- For ECU diagnostics, we integrated the UDS stack (ISO 14229 and ISOTP/ISO15765). Fault code memory (FCM) was also integrated.
- Complete ECU reprogramming sequence was tested with VFlash template.
- Documentation for SWRS, high-level design, MISRA C- 2012 report, unit test report, module test report, and functional test report were provided to the customer.
- We have validated the solution with CAPL script at our end. The customer also validated the same using their proprietary tools.
Embitel Impacts:
Due to our expertise in secure bootloader development, we could complete the project in the strict timeline provided by the customer. Our ready-to-integrate network and diagnostics stacks such as CAN, LIN and UDS also helped save considerable amount of time.
Tools and Techniques:
Vector CANoe: Used for validation of the secure bootloader
Vflash tool: ECU reprogramming sequence was validated using Vflash tool
Microchip Compiler Environment MPLab IDE- Used for development and debugging
Tessy Tool: Used for unit testing


