About the Customer:
Our customer is an automotive connectivity solutions provider that specializes in developing the hardware and software of digital cockpits. They’ve made their mark through successful collaborations with leading automotive brands in Germany.
Business Challenges:
The customer had engaged us to deliver multiple Trusted Applications, each tailored to specific functional and security needs.
Their SoC platform mandated that all TAs be signed, which meant that our team in Germany needed to establish a secure, scalable signing process to meet those requirements.
Why should TAs be signed?
Unsigned TAs pose serious security and compliance risks that can undermine the integrity of an entire automotive software system.
Here’s an overview of the risks it can pose:
- Compromise sensitive data such as cryptographic keys, user credentials, certificates, and vehicle data.
- Malicious actors could insert harmful code, impersonate trusted TAs, and gain unauthorized access to critical vehicle functions.
- Unsigned or modified TAs could disable existing safeguards, opening attack surfaces within the system.
- Failure to implement robust signing mechanisms could result in non-compliance with ISO 21434 or UNECE WP.29, potentially delaying or blocking product release in regulated markets.
- Without signing, there is no cryptographic proof of authorship or version control, making incident response and audits difficult or impossible.
Our automotive cybersecurity experts developed a secure and automated solution to prevent these risks.
Embitel’s Solution:
Our cybersecurity team in Germany has vast experience in developing trusted applications and public key infrastructure solutions.This helped us understand & translate the client’s needs into technical requirements.
The consultation sessions with the customer helped us understand that developing an image signing solution could help their TAs become Tamper-Proof.
Our solution included:
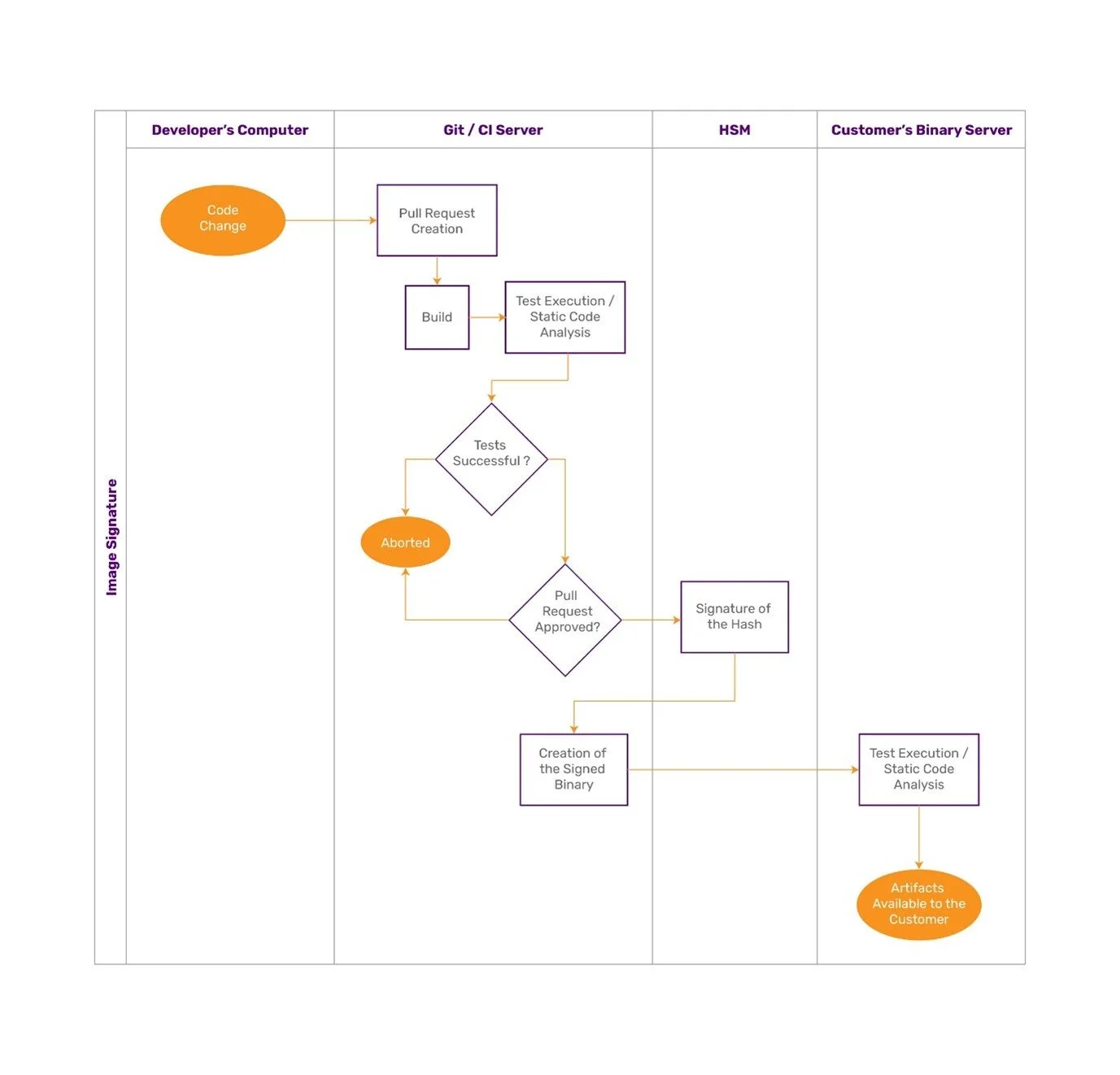
TA Image Signing Pipeline
Key Generation and Provisioning
The process of signing TAs begins with the generation of a private public key pair called the TA Verification Key.
- The public key is securely transferred and provisioned into the target ECU.
- The private key is retained by our team and used excessively for signing in their PKI infrastructure.
Triggering Pull Request
Trusted Applications are version-controlled in a secure GitHub repository.
Only authorized personnel—following the 4-Eyes Approval Principle—can initiate a pull request to move the TA to the next stage.
This pull request triggers an automated CI/CD pipeline that performs:
- Unit testing
- Static analysis
- Policy enforcement checks
Automated Signing
Once verified by performing the tests, the pipeline securely signs the TA image using TA Verification Private Key.
The solution can support any type of image with signing workflows integrated directly into the build process.
The CI/CD pipeline itself performs the signing, ensuring traceability and eliminating manual risks.
Secure Delivery & Integration
Signed artifacts such as the TA, signature, and optionally the certificate chains are uploaded to the customer’s data platform through secure channels.
Verification of TA on the ECU
Before execution , the ECU’s TEE validates the TA using the provisioned TA Verification Public Key. The ECU accepts and runs the TA only if:
- The digital signature is valid
- The TA has not been modified
- It complies with the defined versioning and trust policies
This ensures that only authenticated, unaltered TAs from our team are allowed to execute. This protects the TA against tampering, impersonation, and supply chain attacks.
Embitel Impact:
- The customer gained cryptographically enforced confidence in the authenticity and integrity of each deployed TA.
- The solution helps enforce the chain of custody, supports secure over-the-air deployment, and aligns with OEM cybersecurity expectations.
- The solution helps the customer in secure deployment and aligning with regulatory standards like ISO 21434 and UNECE WP.29.
Tools and Techniques:
- GitHub
- Hardware-Security Module (HSM)


