About the Customer:
Our customer is an automotive software company that develops unified operating system, digital services, and automated driving technologies to enable software-defined vehicles.
Their system integrated a central SoC with specialized hardware, including One-Time Programmable (OTP) memory, which is only accessible from the Trusted Zone.
Business Challenges:
The client needed a reliable solution to leverage OTP memory for two primary security purposes:
- Storing the unique ECU identifier (FAZIT ID) and
- Enabling anti-rollback protection
Moreover, rollback protection was critical to prevent foreign interferences from reinstalling outdated ECU software versions with known vulnerabilities.
Developing the solution came with several hurdles.
The OTP memory was hardware-specific and could not be reused across different platforms without changes. Additionally, any incorrect write operation to OTP could permanently damage the ECU, making testing extremely risky.
Moreover, the team had limited access to production hardware, and each test consumed the OTP space irreversibly, this renders the ECU that makes it unusable for further trials.
Embitel’s Solution:
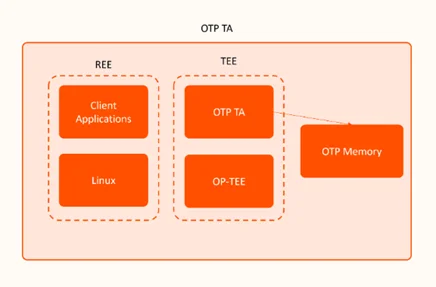
Leveraging our expertise in Trusted Application (TA) development, our team in Germany designed and implemented a secure software TA that mediated access to the OTP memory within the Trusted Execution Environment (TEE). This helped the client ensure:
- Controlled Access via Trusted Application: The TA ensured all OTP read/write operations were tightly controlled, preventing unauthorized access or accidental overwrites.
- Virtualized Testing with OP-TEE: To minimize the risk of damaging production hardware, the team used OP-TEE with QEMU to emulate the target hardware in a virtualized environment. This also enabled exhaustive unit and integration testing before deployment.
- Automated Validation: Automated test suites were created to run after every code change, ensuring stability, consistency, and faster iterations.
- Final Hardware Verification: Only when confidence was established in virtualized tests did the team perform limited validations on real ECUs, minimizing waste of critical hardware units.
Embitel Impact:
The project delivered a lightweight yet critical Trusted Application that became part of the client’s It enabled two essential capabilities:
- Secure storage of immutable ECU identifiers and
- Robust anti-rollback protection through version management in OTP memory.
Although compact in scope, this solution was instrumental in ensuring platform integrity and protection against common attack scenarios.
Tools and Techniques:
- Kinibi Trusted Execution Environment on production hardware
- OP-TEE with QEMU for virtualized testing
- C / C++ for Trusted Application development
- Customer SDK and GlobalPlatform APIs for integration and standardization


