
- Automotive & EV▼
- IoT▼
- Digital Solutions▼
- Industries▼
- Technology▼
- Digital Growth Enablers▼
- Commerce & Experience Services▼
- Success Stories▼
- Thought Leadership▼
- Industries
- AI/ML▼
- Company▼
- Careers▼
- Contact Us
- Blog






Penetration Testing or pentesting is a form of security testing that involves simulation of real-world attack scenarios to test cyber defense of digital infrastructures. The process helps businesses identify exploitable vulnerabilities and loopholes in their products, existing infrastructure and security mechanisms and fix them with efficient solutions.
With over a decade of experience as a trusted technology partner for Fortune 500 companies, we go beyond identifying vulnerabilities. Our expertise helps businesses strengthen their overall security posture and ensure compliance with global cybersecurity regulations. We take pride in delivering measurable, secure, and compliant outcomes across complex environments.
A server hosting provider required comprehensive penetration testing to assess their security posture and identify potential vulnerabilities across their infrastructure.
We conducted thorough penetration testing that uncovered multiple critical vulnerabilities. The assessment revealed a chain of exploits including payment bypass mechanisms, internal DNS resolver manipulation, and ultimately the capability to redirect internal network traffic to external attacker-controlled systems. Additionally, several OWASP Top 10 vulnerabilities were identified, including a blind XSS injection that provided access to the web support admin panel.
A major social network platform with approximately 5 million simultaneous users required penetration testing to evaluate their security infrastructure and identify potential vulnerabilities.
We conducted a comprehensive security assessment that identified a critical cache poisoning vulnerability within the platform's infrastructure. Given the severity and potential impact on system availability for millions of active users, the vulnerability was carefully documented without exploitation to prevent service disruption.
Our abilities extend beyond basic end point penetration testing. We support enterprises, OEMs, and Tier-1 suppliers across their complete development lifecycle.

Simulate real-world automotive attacks on ECUs and in-vehicle networks to uncover security gaps and ensure compliance with ISO/SAE 21434 and UNECE WP.29 standards. Beyond identifying vulnerabilities, we deliver pragmatic remediation strategies, risk-prioritised findings, and actionable insights that empower engineering teams to harden vehicles against sophisticated adversaries.
Assess firmware, communication protocols, hardware interfaces, and microcontroller logic to detect flaws that traditional testing misses. We blend in protocol-level analysis, reverse engineering techniques, and hardware-centric attacks to reveal systemic vulnerabilities and reinforce resilience across the full stack of embedded and IoT components.


Strengthen system integrity and ensure compliance with evolving cybersecurity standards of Industry 4.0. Simulate realistic threat vectors like control logic abuse, network segmentation bypass, and protocol manipulation to reveal hidden attack paths and configuration weaknesses in industrial control systems (ICS), SCADA networks, and operational technology (OT) environments.
Integrate comprehensive security measures throughout application lifecycle to detect misconfigurations, insecure APIs, and privilege vulnerabilities across cloud and web environments. Scrutinise CI/CD pipelines, API gateways, and microservices architectures to identify and remediate critical security gaps before they impact customers or operations.


Emulate advanced, real-world attack campaigns that evaluate your organisation’s end-to-end security posture under realistic conditions. We mirror sophisticated threat actors to uncover hidden attack paths, validate detection and response capabilities, and identify high-impact risks, delivering actionable insights to strengthen resilience across people, processes, and technology.
We follow globally recognized penetration testing frameworks such as OWASP, PTES, and NIST SP 800-115 to ensure accurate, repeatable, and compliant testing.
Additionally, our operations uses AI-assisted analysis that accelerates vulnerability correlation, prioritization, and anomaly detection without replacing expert manual testing.
Our penetration testing services follows a structured approach, which includes:
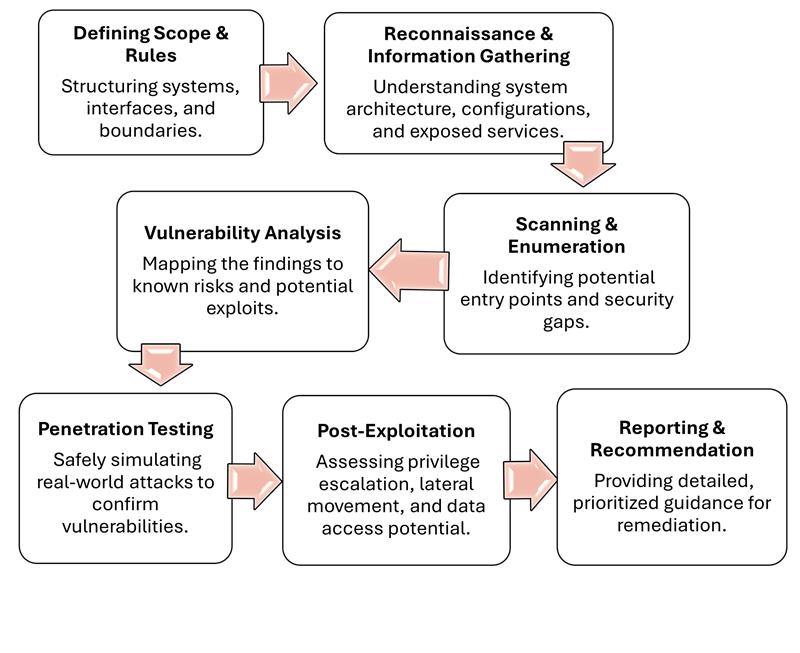
Helps detect vulnerabilities and fixes before they become entry points for critical cyber intrusions.
Proactively mitigates breaches that could lead to downtime or reputational damage.
Supports compliance with ISO/SAE 21434, UNECE WP.29/R155, NIST 800-53, IEC 62443, and other security frameworks.
Enhances overall security posture through regular testing, analysis, and remediation strategies.
Penetration testing services involve simulating real-world cyberattacks on digital systems, networks, or applications to find exploitable vulnerabilities before malicious actors do. The process offers actionable insights that help enterprises strengthen their security posture, validate defence mechanisms, and ensure compliance with cybersecurity standards.
A vulnerability scan automatically shows known weaknesses within systems or networks, offering a broad view of potential risks. In contrast, a penetration test goes a step further by manually exploiting those vulnerabilities to assess their real-world impact. While vulnerability scanning is diagnostic, penetration testing is demonstrative, it proves how deep an attacker can go.
Penetration testing can be performed across multiple domains, including:
Security experts use a combination of automated and manual tools to achieve accurate, in-depth testing. Commonly used tools include Metasploit, Burp Suite, Nmap, Wireshark, and custom-built scripts for specialized environments such as automotive ECUs, embedded firmware, and cloud infrastructures.
Enterprises should perform penetration testing at least once a year or after any major infrastructure or application update. Continuous testing is recommended for organizations undergoing frequent deployments, adopting cloud transformations, or managing critical data. Regular assessments ensure that newly introduced systems and updates do not create fresh vulnerabilities.
When conducted by experienced professionals, penetration testing is designed to minimize disruption. Tests are carefully scoped and performed during controlled windows to avoid downtime. In sensitive environments like production or automotive systems, simulations are executed in isolated or mirrored setups to ensure zero operational impact.
Static Application Security Testing (SAST) analyses source code for vulnerabilities before an application is deployed, while Dynamic Application Security Testing (DAST) evaluates the running application in real time to identify exploitable flaws. Both methods complement each other to secure the application throughout its lifecycle—from development to production.
Standard penetration testing engagements adhere to globally recognized frameworks, including OWASP, PTES, OSSTMM, and NIST SP 800-115. These standards ensure a structured, repeatable, and compliant approach to testing, aligning results with industry best practices and regulatory requirements such as ISO/SAE 21434, UNECE WP.29, and GDPR.