“Penetration testing in automotive security refers to ethical hacking of a vehicle’s security system to spot vulnerabilities that could become a potential entry point for cyber exploitation.”
As the world accelerates towards connected mobility, software-enabled features have become the driving force of automotive innovation. Vehicles that once ran on isolated machines now depend on complex digital ecosystems that communicate through networks, cloud platforms, and external interfaces.
While these advancements enabling smarter mobility have witnessed an exponential growth trajectory, the number of cyber vulnerabilities has also increased significantly. A study recently highlighted that without proper security testing, a vehicle may host over 500 vulnerabilities that can be remotely exploited at any time.
Sounds terrifying, right? This is where penetration testing comes into the picture!
This article will deep dive into the complex vulnerabilities of automotive cybersecurity, highlighting how penetration testing can be an effective all-in-one solution.
What is Penetration Testing?
Penetration testing serves as a proactive offensive measure designed to identify, exploit, and resolve security gaps before attackers can take advantage of them. It involves simulation of real-world cyberattacks on a system, network, or application to identify weaknesses before malicious actors do.
In the context of automotive systems, penetration testing targets embedded components like ECUs, gateways, and telematics units, along with connected mobile apps and backend cloud infrastructure. The primary aim of such testing is not just to find vulnerabilities but to understand how they could be chained together to compromise vehicle safety, data integrity, or remote functionality.
Difference between Penetration Testing and Vulnerability Scanning
While discussing automotive security testing alongside penetration testing, another commonly mentioned term we often come across is vulnerability scanning. Although both have similar scope and help identify system weaknesses, they differ in purpose, depth, and execution.
Vulnerability scanning is typically an automated process that detects known flaws by comparing a system against a database of common vulnerabilities. It’s often used as a preliminary step in penetration testing to identify outdated firmware, open ports, or misconfigurations. However, it does not determine how these weaknesses can be exploited or what real-world impact they may have on vehicle security.
Penetration testing, in contrast, goes far beyond detection. It involves both manual and automated techniques where ethical hackers simulate real-world attacks to validate and exploit vulnerabilities. In automotive systems, this involves assessing potential flaws in various components.
| Aspect | Vulnerability Scanning | Penetration Testing |
| Approach | Automated scanning | Manual and automated simulation |
| Depth | Surface-level detection | In-depth exploitation and analysis |
| Objective | Identify known vulnerabilities | Assess real-world exploitability |
| Skill Requirement | Minimal human expertise | Requires ethical hacking expertise |
| Frequency | Regular and continuous | Periodic or project-based |
| Output | List of potential issues | Detailed report with risk impact and remediation |
| Use Case in Automotive | Detect outdated firmware or misconfigurations | Test ECU, network, and cloud exploit paths |
| Goal | Awareness | Validation and prevention |
How Penetration Testing Works in Automotive Systems
Unlike traditional IT environments, vehicles today combine multiple domains, including embedded, cloud, and mobile. This makes testing a multi-layered process that involves hardware, communication protocols, and backend services.
To ensure the overall mirroring of the attacker’s mindset, penetration testing follows a methodical process. However, the strength of the attack can only be determined when a vehicle is seen as an ecosystem of linked trust boundaries and clearly mapped with the potential attack surface.
Automotive Attack Surface
In modern vehicles, the surface is generally broad and layered. It spans hardware, networks, wireless links, cloud services, and human-facing workflows
The following breakdown will help you get a clearer picture of where the attacks are usually targeted and their potential penetration:
| Component | Examples | Typical threats | Risks |
| In-vehicle networks & buses | CAN, LIN, FlexRay, MOST, Automotive Ethernet | Message injection, replay, bus flooding (DoS), timing attacks | Erratic vehicle behaviour, loss of control, Denial of Service for safety functions |
| Electronic Control Units (ECUs) & firmware | Powertrain ECU, ADAS ECUs, BCM, infotainment ECUs | Vulnerable firmware, insecure boot, hardcoded keys, debug interfaces | Persistent compromise, firmware tampering, privilege escalation |
| Gateways & domain separation | Central gateway, zone controllers | Weak filtering, improper routing, lateral pivoting | Cross-domain attacks from infotainment to safety domains |
| External wireless interfaces | Bluetooth, Wi-Fi, NFC, cellular modems, keyless entry | Pairing abuse, replay, fuzzing, remote exploitation | Remote entry, unauthorized commands, privacy breaches |
| V2X / telematics communications | DSRC, C-V2X, 5G V2X, telematics units | Spoofing, replay, eavesdropping, message flooding | Misleading vehicle decisions, traffic disruption, safety hazards |
| Onboard diagnostic & service ports | OBD-II, JTAG, UART, maintenance connectors | Direct ECU access, debug shells, secret extraction | Full system access, secret exfiltration, firmware manipulation |
| Mobile apps & companion services | Owner app, paired devices, BLE peripherals | Weak auth, token theft, insecure storage, API misuse | Remote vehicle control, user privacy loss, account takeover |
| Cloud backend & OTA infrastructure | Telematics cloud, OTA servers, fleet APIs | Broken auth, insecure APIs, unsigned updates, rate limiting issues | Fleet-scale compromise, malicious OTA deployment, data breach |
| Third-party components & supply chain | Tier-1/Tier-2 modules, libraries, CI/CD pipelines | Vulnerable libs, poisoned updates, insecure supplier processes | Widely propagated vulnerabilities, persistent supply-chain backdoors |
The Phases of Automotive Penetration Testing
Now that you might have a clear idea of different components at risk of cyberattack, let’s understand the process of automotive penetration testing.
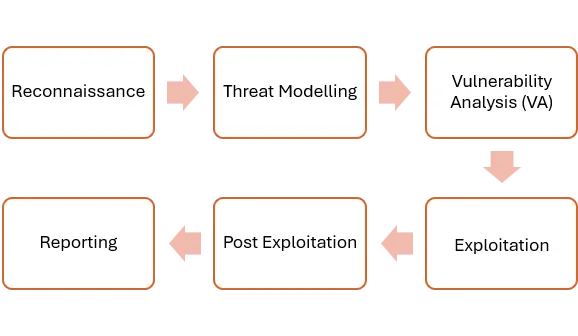
Automotive penetration testing follows a staged sequence that mirrors an attacker’s pattern that includes gathering, modelling, exploiting, moving and remediating. Each phase is tuned for embedded constraints, Functional Safety (FuSa) and the hybrid cloud–mobile–vehicle environment.
- Reconnaissance
- Threat Modelling
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Attempting lateral moves to assess initial foothold to reach ECUs, telematics, or fleet management services.
- Implanting a backdoor in firmware
- Abusing update channels,
- Stealing credentials to maintain access.
- Reporting
This step involves collecting critical data of the target without intrusive actions. The primary objective of this step is to create a prioritised map of high-value assets and likely attack vectors.
Experts usually rely on supplier documentation, public firmware repositories, companion app analysis, passive network sniffing, and physical inspection to collect the information.
Next, experts translate the collected data into potential threats, also known as threat modelling.
Threat modelling basically helps identify the attack paths that could lead to safety impact (e.g., spoofing a brake request) or large-scale effect (e.g., malicious OTA).
This phase also involves setting up the Rules of Engagement (RoE), defining safety kill switches, and aligning test depth with allowed risk. In automotive, threat modelling must also consider FuSa implications (ISO 26262) and regulatory constraints (WP.29).
Next, combining automated scanning and manual inspection, experts enumerate exploitable weaknesses in vehicle systems. This includes targeting firmware analysis, protocol fuzzing on CAN/UDS, and assessing the mobile/cloud authentication flows.
Moreover, active tests are performed with strict safety controls and, where possible, on bench setups or virtualised vehicle models.
This stage involves attempts to exploit discovered weaknesses by authenticating as a privileged user, injecting safety-critical messages, or tampering with OTA images.
Every exploit in this stage produces a controlled Proof of Concept (PoC) demonstrating impact without harming equipment or people.
If exploitation succeeds, the next concern is whether an attacker can become persistent: This stage involves the activities that experts perform after exploiting vulnerabilities. This generally includes:
Once the whole pentesting process is complete, it must be precisely reported to decide on actionable items. The reports basically include PoC artefacts, suggested fixes (short-term mitigations and long-term secure design changes), and validation criteria.
Penetration Testing in the Automotive SDLC
In traditional automotive engineering, security assessments were often performed near the end of development. However, as the automotive technology advanced, so did the vulnerabilities, introducing new risks with every iteration and update This makes post-deployment security assessment a reactive approach, inadequate for connected vehicles.
To ensure the earliest detection of these software vulnerabilities, OEMs and Tier 1s prefer opting for a “shift-left” strategy that suggests embedding security validated via penetration testing in every stage of the automotive Software Development Lifecycle (SDLC).
A structured way to visualize this integration is through the V-Model, where every development phase aligns with a corresponding validation step.
V-Model Integration of Penetration Testing
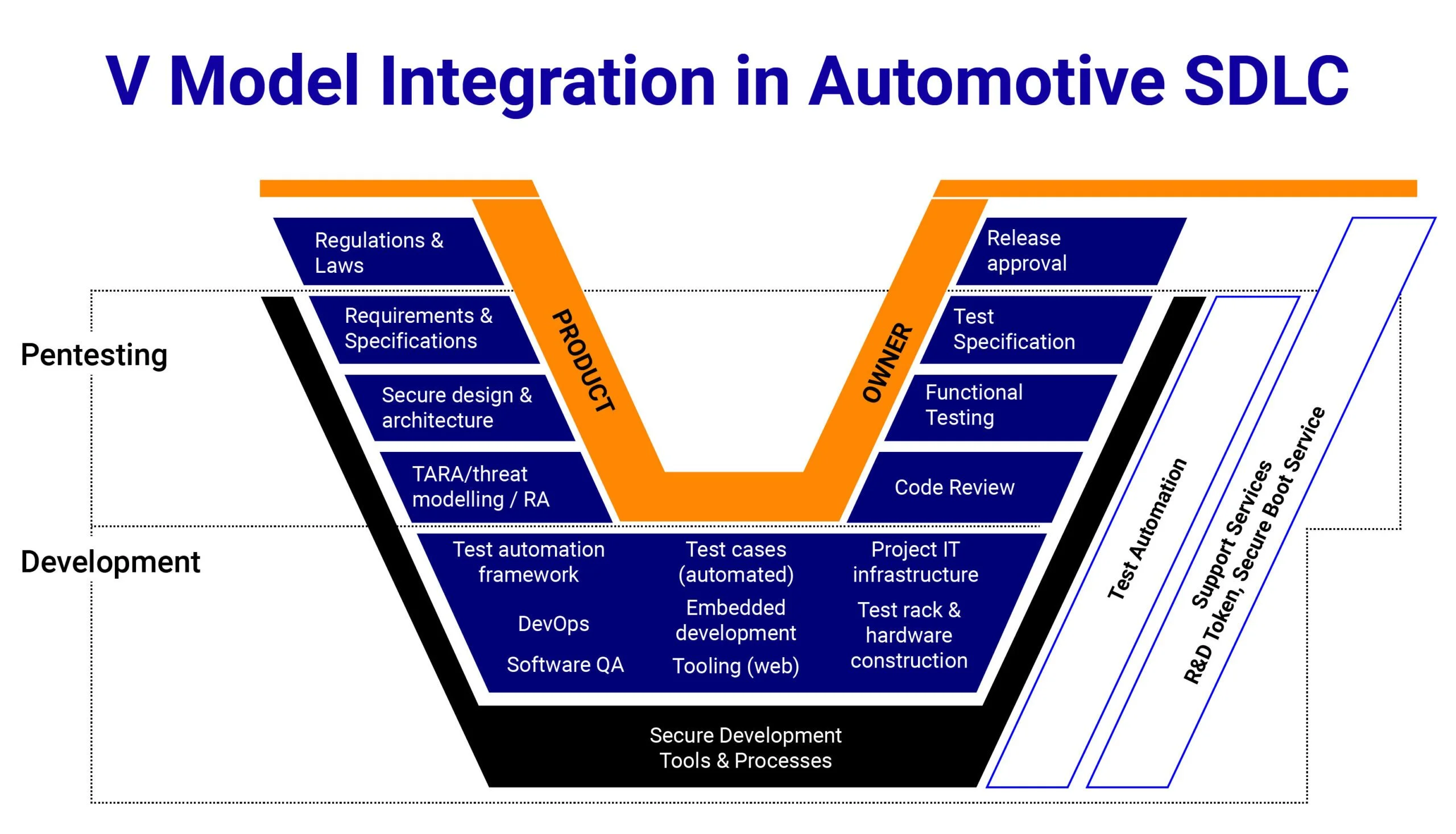
The V-model framework is one of the most popular methodologies for security testing automotive software throughout its development lifecycle.
The initial “V” in the methodology stands for verification and validation, which separates the automotive development process into two key phases. The left side focuses on defining requirements, designing functions, and developing the software, while the right side emphasises testing, verification, and validation activities leading up to the final release.
Penetration testing fits naturally into each stage of the framework. During the requirement and design phases, experts collaborate with engineers to identify potential attack surfaces, define security requirements, and perform threat modelling.
Further, as development progresses, penetration testing validates software modules, communication protocols, and integration points for vulnerabilities before moving to higher stages. On the validation side, system-level tests replicate real-world attack scenarios to confirm that implemented countermeasures are effective.
Standard Pentesting Approaches to Test Automotive Systems
By now you might have got a clear idea of how the penetration testing works in the automotive environment. Nevertheless, the approach to conduct the penetration tests are further categorised into the three different categories based on project scope and visibility.
| White Box Testing | Black Box Testing | Grey Box Testing |
In this approach, pentesting experts are given complete access to internal system details such as source code, architecture diagrams, or firmware. This transparency enables deep analysis of potential weaknesses within logic, cryptographic implementations, and access control mechanisms. It’s often used during the early development or validation stages when the goal is to ensure robust defence from the inside out. |
In the black box testing approach, the tester acts like an external attacker with no prior knowledge of the system.
The primary objective in this approach is to simulate real-world intrusion attempts by probing exposed interfaces, like OBD-II ports, telematics, or APIs, to identify exploitable gaps. This approach is valuable for assessing how well the system resists unauthorised access in production-like conditions. |
As the name suggests, the grey box approach is a hybrid model; grey box testing combines white and black box methods.
Testers have full access to critical components with limited system insights. This approach aims to strike a balance between realistic attack simulation and efficient vulnerability detection. This makes the approach most practical for modern automotive systems blending hardware, software, and cloud connectivity. |
Conclusion
The future of mobility is undeniably digital, driven by intelligent software, real-time connectivity, and autonomous decision-making. However, with every new feature will come a new frontier of risk.
Penetration testing stands at the core of securing the software-led automotive evolution. It acts as a bridge between innovation and assurance, exploring how systems truly behave under attack long before real adversaries get the chance.
In the road ahead, penetration testing won’t just protect systems; it will define the trust that powers the next generation of connected mobility.


