Every update to the vehicle software adds capability. It also adds risk. A new feature today can become a new vulnerability tomorrow.
“In the year 2024 alone, more than 6 million connected vehicles were exposed to remotely exploitable vulnerabilities many of which originated in third-party ECUs or cloud misconfigurations.”
Given the considerable risk vectors, regulations like UN R155 and ISO/SAE 21434 has now established threat modelling practices as mandatory.
Among these practices, penetration testing and red teaming are the most distinct offensive security exercises often thought to be same. Nevertheless, both these exercises widely differ in scope, applications and goals.
This article will deep dive into how these practices fit within automotive threat modelling. Further, we will break down their unique purposes, methodologies, and how they collectively strengthen the security posture of modern vehicles.
Threat Modelling in Automotive Cybersecurity
With regulatory compliance becoming more stringent, the question now becomes: how do automotive engineers and cybersecurity teams translate these evolving expectations into actionable security practices?
Typically, threat modelling in automotive systems does not follow a single spoofing mechanism. Instead, it draws insights from multiple structured approaches such as:
- Attack trees,
- STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial, Elevation of privilege), and
- Risk-centric frameworks like Process for Attack Simulation and Threat Analysis (PASTA)
These methods enumerate attacker goals across vehicle ecosystems targeting mobile, cloud and supply-chain domains. Additionally, it allows mapping of assets (ECUs, gateways, telematics servers, OTA pipelines), threat agents, and possible attack steps which is then fed directly into targeted pen tests or red-team objectives.
Where Penetration Testing and Red Teaming Fit in the Vehicle Lifecycle
Today’s vehicles are built on complex software stacks, from ECUs to cloud backends.
When a safety-critical component fails, it doesn’t stay isolated. It can affect the entire ecosystem.
To avert such incidents, both penetration testing and red teaming fall under the offensive validation phase that models threat and tests them against real-world attack scenarios.
While pentesting aims to identify vulnerabilities within a system, red teaming focuses on testing the organization’s overall detection and response capabilities. Let’s breakdown each one by one.
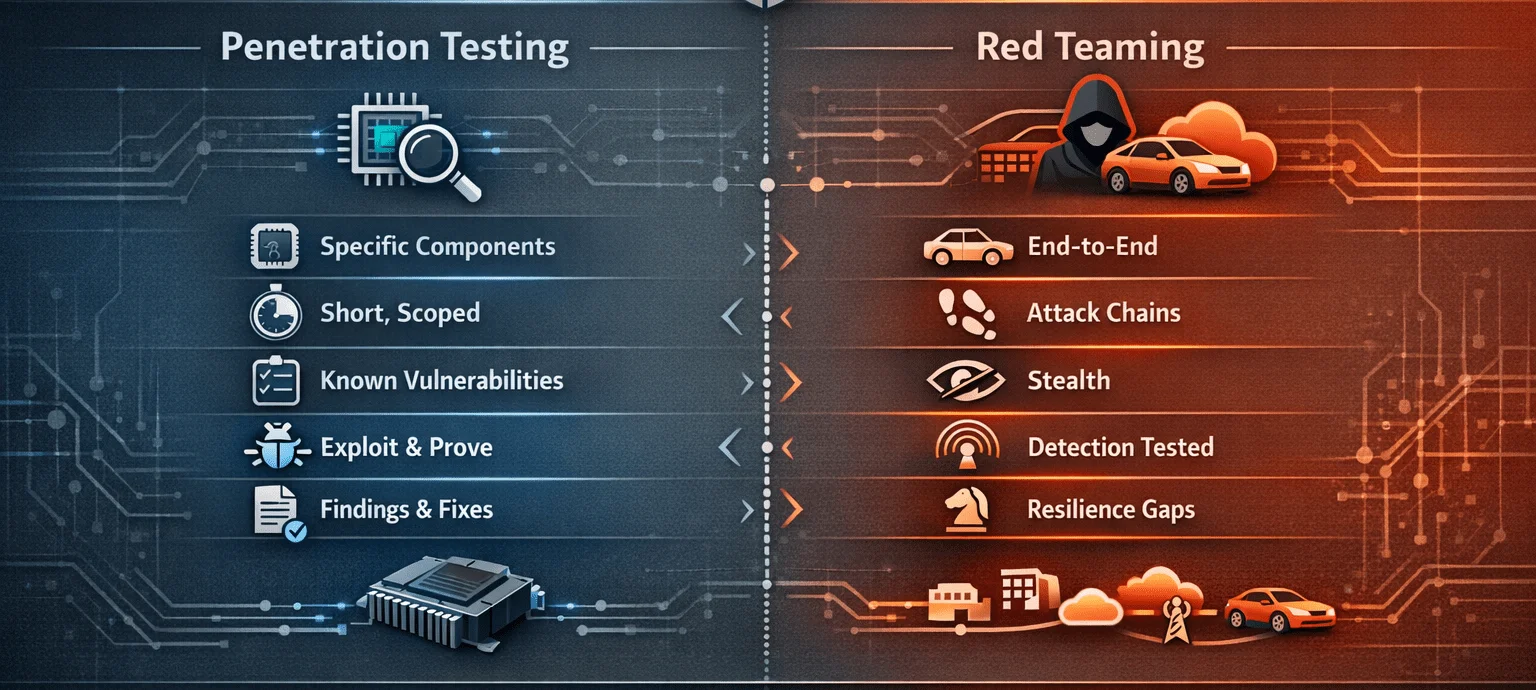
Penetration Testing
Pentests are scoped, technical assessments focused on finding and proving component-level vulnerabilities. It is a structured, time-bound process that uses a platform or a tool to identify, exploit, and report vulnerabilities in a specific component, network, or system. Its primary objective is to reveal technical flaws before attackers do, answering practical technical questions around:
- What can an attacker exploit this interface or component?
- How is it exploited?
- What is the proof-of-concept?
Meanwhile, the deliverables produced in this operation provides concrete and tactical list of findings ranked by severity, reproducible PoCs, remediation recommendations, and (often) a retest once fixes are in place.
Pentesting Application in Automotive Systems
In the automotive ecosystem, penetration testing targets a wide range of components, including:
- ECU firmware: To identify weak cryptography or buffer overflows with reverse engineering techniques
- In-vehicle networks (CAN, LIN, Automotive Ethernet): To test for message injection or spoofing vulnerabilities
- Telematics control units (TCU): To assess GSM/Wi-Fi interface exploits and OTA update endpoints
- Cloud APIs and mobile apps: To identify token exposure, insecure authentication, and misconfigurations
Red Teaming
Red Teaming is a goal-oriented adversary-emulation exercise that attempts to achieve realistic objectives through any feasible attack path across domains.
It expands the lens of penetration testing. Instead of focusing primarily on technical flaws of a single component, a red team emulates realistic adversaries and their objectives. It blends technical exploits with tactics like lateral movement, persistence, covert exfiltration, and sometimes physical or social engineering.
The outcomes of the operations are strategic, and the reports generated with highlight its key objectives like:
- Attack narratives (how the adversary moved and why),
- Detection timelines,
- Gaps in logging and telemetry,
- Recommendations to improve monitoring and IR playbooks, and
- Prioritized security investments required to increase resilience
Red Teaming Automotive Applications
The red teaming automotive application extends more than regular digital exploits, it simulates end-to-end, multi-domain attack chains that mirror real-world adversarial behaviour across the vehicle, cloud, and supply chain ecosystems.
For instance, a red team exercise might begin with a phishing campaign targeting supplier engineers. It may help them gain initial access to backend cloud environments followed by firmware tampering during over-the-air (OTA) updates and culminating in a coordinated in-vehicle intrusion. Such simulations help OEMs and Tier-1 suppliers validate how effectively their defence-in-depth mechanisms.
Moreover, beyond offensive simulation, automotive red teaming also acts as a blue-team maturity assessment. It evaluates whether detection mechanisms (SIEMs, IDS/IPS, or in-vehicle anomaly detectors) can flag abnormal behaviour in time, and how effectively incident response (IR) procedures can contain it.
This adversarial emulation is particularly relevant for connected fleets, where latency in detection can translate to large-scale exploitation.
Key Differences Between Penetration Testing and Red Teaming
| Feature | Penetration Testing | Red Teaming |
|---|---|---|
| Objective | Find and exploit vulnerabilities | Simulate realistic adversary, test end-to-end attack path |
| Scope | Defined systems/applications | Broad with systems, people, processes and physical access |
| Timeframe | Short (days to a few weeks) | Longer (weeks to months) |
| Detection focus | Minimal visibility to defenders accepted | Emphasis on stealth, evading detection |
| Deliverables | Vulnerability list + remediation guidance | Attack timeline, detection/response gaps, strategic findings |
When to Use: Pentesting vs. Red Teaming
By now, the differences between penetration testing and red teaming should be evident.
But it’s equally important to understand that they are not competing exercises. They complement each other, and each serves a distinct purpose. Their value depends on when and where they are applied within the vehicle development or deployment lifecycle.
Penetration testing is typically conducted during early or mid-development stages when individual ECUs, IVIs, TCUs, or backend systems are integrated and need assurance against exploitable weaknesses.
Red teaming, on the other hand, is better suited for mature systems or organizations aiming to validate their defense-in-depth strategy across the entire ecosystem. It simulates end-to-end adversarial campaigns that test not only the technology stack but also the detection and response readiness of SOCs, SIEMs, and blue teams.
Integration of Red Teaming & Penetration Testing into the Threat Modelling Lifecycle
While the conceptual differences between red teaming and pen testing are significant, leading OEMs and Tier-1 suppliers often adopt a cyclical approach. They execute penetration tests during integration and conducting red team operations post-deployment.
Findings from penetration tests feed tangible evidence into the threats of software, highlighting exploitable weaknesses, refining attack trees, and updating risk scores based on real-world exploitability. Meanwhile, insights from red team exercises improve the process by revealing gaps in visibility, response workflows, and inter-domain dependencies that static threat models alone cannot uncover.
Together, these exercises close the feedback loop of automotive cybersecurity management. Each iteration of testing helps recalibrate the Threat Analysis and Risk Assessment (TARA), optimize security controls, and strengthen the overall Cybersecurity Management System (CSMS).

