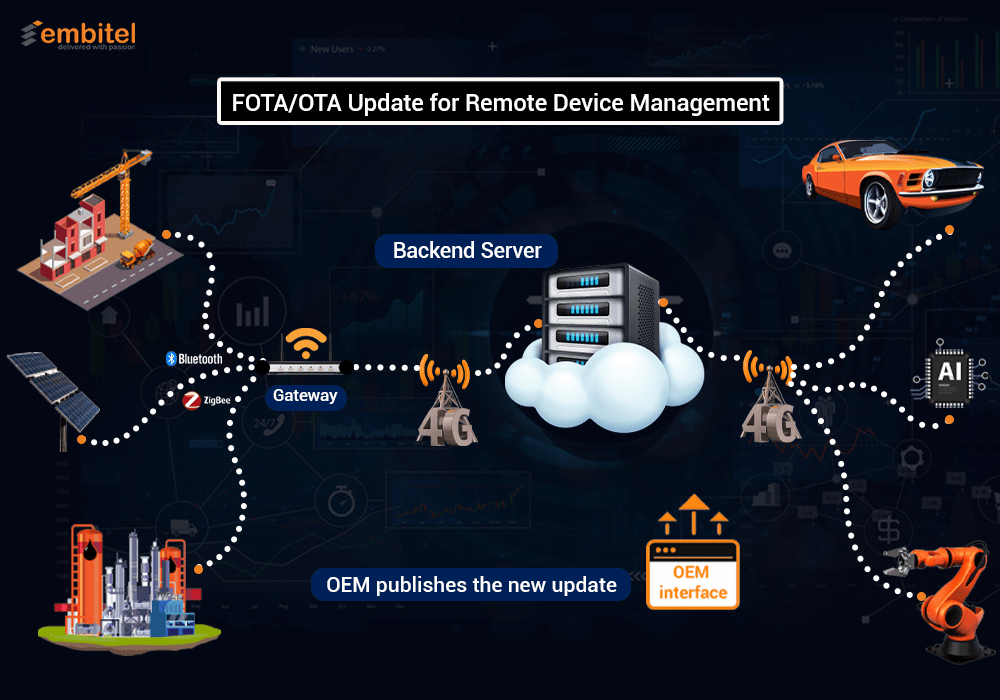
FOTA Update | Firmware Over the Air
Delivering wireless updates for your IoT Devices





Embitel’s FOTA Update Services provide a complete framework for secure and controlled firmware deployment across automotive ECUs and connected devices. The solution includes bootloader development, secure firmware packaging, logical device grouping, campaign scheduling, and rollback mechanisms.
Updates are atomic, minimizing downtime and preventing incomplete or corrupted installations. The platform is designed for multi-tenant access, supports automated test execution, and is resilient to real-world failures, including power loss, memory corruption, and communication errors. With cloud-based deployment scripts and encryption at every layer, it is built for scalable, production-grade rollouts.
Features of Our FOTA Update Solution for Remote Device Management
Comprehensive Remote Device Management
- Remote device management through OTA software updates
- Scheduling, release and reporting of the firmware build versions through a web server interface solution
Custom OTA Release Management with Device Grouping
- Controlled and customized OTA software release management, through logical device grouping based on project requirements
Code Signing for Secure Firmware Updates
- Code signing to ensure the trustworthiness (data integrity & source authentication) of each firmware image being updated
Downtime Reduction
- Ensuring that device downtime is minimized during updates
Complete and Error-Free Updates
- Ensuring that every session of FOTA update is complete and atomic; so that the firmware update does not end in an incomplete/broken state
Types of FOTA Update Offerings at Embitel


Firmware Over the Air – Design and Development Services
- Flash Memory Selection – NOT, NAND & more, based on your project requirements.
- Integration of Wi-Fi/Bluetooth/GPRS/GSM modules for secure communication between the FOTA server and the target devices.
- Design and development of Firmware and integration with IoT protocols such as MQTT, CoAP; HTTPS & SSL for secure data exchange; FTP/FTPS for file transfer.
- Selection of specific encryption methods to check the sanity of the update package.
- Deciding the level of FOTA update required (At the whole system level, OS and application level, or only at the application level).
- Bootloader development to enable firmware download and reprogramming on the application device.
- Design and development of the FOTA management server interface and other GUIs to build/schedule/deploy/manage the update package.
- Design and development of the interface (GUI) to build/schedule/deploy/manage the update package.
- Tracking as well as reporting the successful instances of firmware updates.
- Integration of Firmware Rollback mechanism to mitigate any failure or bug detected during Over the Air update.
- Development of Automated test frameworks to enable devices to perform self-test & send status reports, at the end of an update.
After design and development of the FOTA feature for your connected devices, the hardware and software components are subjected to the following pre-production test-case scenarios:
- Power Failure
- Communication Failure
- Memory Corruption
- Failure to boot the new firmware image
- Flashing of a corrupted firmware image
- Failure to retrieve the information about the configuration & last status of the firmware
We also perform Image self-tests to check if all the firmware functions are working properly.
Embitel’s FOTA Update Stacks – Update Management
Our FOTA Update stacks are designed to compliment the development of your cloud based innovation!

Device Management
Our device management stack conducts operations to deploy FOTA updates to your fleet of IoT devices.
Enhance your device management with Embitel’s FOTA service offerings:
- Seamless Updates: Instantly deploy software and firmware updates across your device fleet.
- Remote Configuration: Adjust settings in real-time without physical access.
- Proactive Monitoring: Monitor device performance and health for proactive maintenance.
- Robust Security: Ensure authorized updates with top-tier security protocols.

Campaign Management
Optimize your OTA updates with Embitel’s Campaign Management services. Our solution enables you to:
- Plan Updates Strategically: Tailor your update campaigns to meet specific goals and timelines.
- Deliver Updates to the Right Customers: Segment devices for precise targeting, ensuring the right updates reach the right users.
- Real-time Monitoring: Track deployment success and user feedback to optimize updates.

User Management
Embitel’s User Management services - designed for high-volume, multi-tenant environments enables you to have:
- Role-Based Access Control: Efficiently manage users with different roles, ensuring tailored access and permissions.
- Scalable Architecture: Support a large number of users seamlessly, maintaining performance and reliability.
- Centralized Administration: Simplify user management with a single platform for easy monitoring and control.

Cloud Deployment Scripts
Harness the power of Embitel's Cloud Deployment Scripts powered by Terraform for your FOTA updates. Our solution provides:
- Automated Deployments: Ensure consistency and efficiency with infrastructure as code.
- Scalability: Easily scale your updates across multiple environments, adapting to your needs seamlessly.
- Version Control: Manage and track changes with precision, reducing risks and improving reliability.
- Rapid Rollouts: Accelerate your update process with quick and efficient deployments.
Embitel’s OTA Firmware Update Accelerator
Our OTA firmware update accelerator is a stack that helps you fast-forward the development of a FOTA solution. This stack is highly customisable and can be configured based on your needs. Using this stack, you can develop scalable and secure FOTA solutions in half the time!
This is a complete FOTA solution with cloud and device side components, secure connectivity modules and Uptane readiness. Read more about the unbeatable benefits of our OTA firmware update accelerator for your automotive development projects.
The device-side FOTA micro stack can be specifically used by customers for accelerating the development of applications such as digital instrument cluster, infotainment system, and digital cockpit. The stack can easily enable FOTA update features in these applications. Read more about our automotive FOTA micro stack.