Certificate management in automotive PKIs (Public Key Infrastructures) refers to the process of handling digital certificates typically X.509 certificates throughout the lifecycle of vehicles. It includes generating, provisioning, distributing, renewing, rotating, and revoking certificates across ECUs, backend services, and V2X endpoints.
While the definition of certificate management process might sound simple; in practicality the story is quite different. Moreover, given the increasing connectivity and attack surface in modern vehicles, the failure to manage the lifecycles of these certificates can lead to unforeseen consequences, such as
- Unauthorized access to the vehicle
- Firmware tampering, and
- Loss of vehicle functionality
This article will explore the crucial process of certificate management in automotive PKIs.
Understanding Digital Certificates and its Role in Automotive PKIs
As the name suggests, certificate management refers to the process of managing digital certificates throughout their lifecycle. It acts like a digital passport that verify the identity of ECUs, backend servers, or diagnostic tools and encrypt communication between them.
How Does Certificates work in PKI Ecosystem
Navigating through the complexities of network security and digital infrastructure, PKI has been a game changer, and digital certificates are its core.
In the last few years, automotive advancements have witnessed the journey of vehicles turning from mobility devices to software-defined vehicles. Nevertheless, this transition would have not been possible without the integration of IoT, and embedded software systems. They allow vehicular components to share data with each other and enable connectivity features like telematics modules, OTA updates, remote diagnostics and many others.
However, this data transfer is not very difficult to manipulate, if not secured with a solid defence mechanism. Hence, all these functionalities rely on seamless communication between ECUs, sensors and PKI backend system.
Digital certificates typically X.509 certificates act as the enabler of trust for unaltered communication between devices, services, and users.
In general, the integrity of data transfer and component interaction is ensured across the entire system, starting with secure-boot trust chain verification and continuing through in-vehicle communication layers such as CAN or Ethernet. Digital certificates enable the mutual authentication and ensure encrypted data exchange.
Certificate Management and its Stages
By now, you probably already have a simple, yet clear idea of what certificate are in PKI ecosystem. Let’s now deep dive and understand what makes it robust and effective.
Automotive certificate management primarily involves handling X.509 certificates, which are the foundation of modern PKI implementations in vehicles and enterprise backend systems. A robust certificate management system acts as a central trust control point, responsible for:
- Issuing certificates to ECUs, gateways, or servers
- Tracking their usage and validity across lifecycles
- Renewing or Revoking certificates automatically to prevent failures
- Retiring obsolete certificates when systems are decommissioned
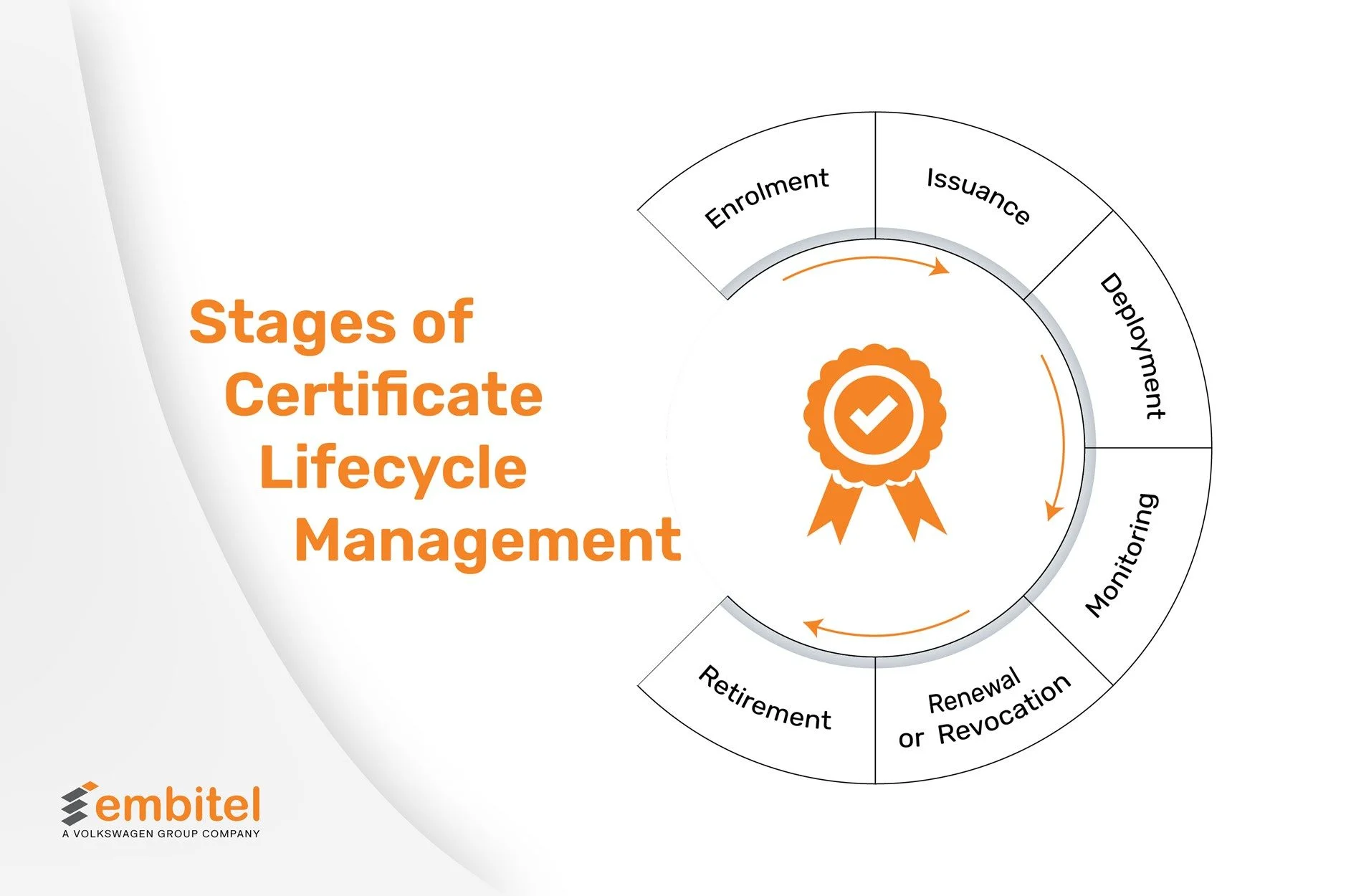
Stages of Certificate Lifecycle Management
Well, as mentioned earlier, the process of the certificate lifecycle goes through steps, and these steps are categorized into five broad stages that go one after another.
- the entity’s public key,
- digital signature of the CA,
- validity period, and
- metadata identifying both the subject
- Certificates are not expired or nearing expiration.
- No revoked or tampered certificates are in use.
- Communication channels remain compliant with cybersecurity standards such as ISO/SAE 21434 and UNECE WP.29.
- Private key compromise
- Employee or system decommissioning
- Change in system role or ownership
- Certificate misuse or error during issuance
Certificate Enrolment
Certificate enrollment refers to registering an ECU, gateway, or backend component to obtain a digital certificate from the Vehicle Public Key Infrastructure (VPKI) or the OEM’s Certificate Authority (CA).
This involves the system generating a Certificate Signing Request (CSR) containing its identity details (e.g., ECU ID, VIN linkage) and public key. The CA verifies this request through predefined authentication and authorization policies, often involving secure manufacturing or provisioning steps and, upon validation, issues the certificate.
Issuance
Once the CA verifies the CSR, it issues an X.509 digital certificate that includes:
Deployment
Certificate deployment involves installing and configuring the issued certificate within the target ECUs, domain controllers, or vehicle backend systems.
This step integrates the certificate into secure communication protocols such as TLS, IPSec, or IEEE 1609.2, ensuring mutual authentication between vehicle components and external services (like cloud servers or charging stations). It also includes setting up trust anchors, intermediate certificates, and validation chains across in-vehicle networks.
Monitoring
After deployment, continuous monitoring of certificates across vehicle fleets and backend systems becomes essential. Automotive OEMs and Tier-1 suppliers often maintain centralized certificate management dashboards to track the validity, integrity, and operational status of all active certificates.
Monitoring ensures that:
Failure to monitor can lead to severe impacts, including vehicle communication breakdowns, diagnostic access issues, or exposure to spoofing attacks.
Renewal/Revocation
Every digital certificate has a limited span of duration; however, to ensure it does not create any interruption in security even after its lifecycle, it is required to be renewed or revoked.
Certificate renewal involves revalidating the identity of the entity and generating a new certificate (either using the same key pair or a new one) that will continue to serve the same purpose. The renewed certificate is reissued by the Certificate Authority and replaces the soon-to-expire certificate.
On the other hand, certificates can also be revoked even ahead of time due to a compromise, misconfiguration, or change in the entity’s status.
Revocation is the process of invalidating a certificate before its expiration. This step is necessary in cases such as
Once a certificate is revoked, it is added to a Certificate Revocation List (CRL) or made accessible via the Online Certificate Status Protocol (OCSP). These mechanisms allow other systems to check the revocation status and avoid trusting compromised certificates.
Retirement
Finally, when a system, device, or service is decommissioned or replaced, the certificates associated with it must also be retired.
This step ensures that no leftover certificates are inadvertently reused or exploited. In enterprise environments, where legacy systems are frequently phased out, having a standardized certificate retirement process is a best practice that closes the loop on secure identity management.
FAQ
What is certificate management?
Certificate management refers to the systematic process of handling digital certificates throughout their entire lifecycle. This includes issuing, deploying, monitoring, renewing, revoking, and retiring digital certificates.
What is the role of X.509 certificates in key management?
X.509 certificates are at the core of modern digital security. They bind a public key to an identity (such as a server, device, or user), enabling encrypted communication and authentication.
What are the different phases of certificate lifecycle management?
The lifecycle of a digital certificate typically includes six key stages:
- Enrollment: The process by which an entity requests a certificate from a Certificate Authority (CA), often by submitting a Certificate Signing Request (CSR).
- Issuance: Once verified, the CA issues a signed X.509 certificate containing identity details and the public key.
- Deployment: Installing the certificate on relevant systems or devices for use.
- Monitoring: continuously checking the status, validity, and expiration of deployed certificates.
- Renewal/Revocation: Renewing certificates nearing expiration or revoking compromised ones to maintain security.
- Retirement: Removing certificates when systems are disposed of.
What is the role of digital certificates in automotive?
In modern vehicles, digital certificates secure in-vehicle communications and external connectivity. They authenticate the identity of ECUs, sensors, telematics modules, and other connected systems, ensuring encrypted communication over automotive networks like CAN and Ethernet.
What is certificate sprawl?
Certificate sprawl refers to the uncontrolled growth and distribution of digital certificates within a network.


