Cryptographic keys are secure digital credentials used to encrypt, decrypt, and authenticate data between two trusted entities. They form the backbone to secure communication and ensure that information exchanged remains confidential and tamper-proof.
While on the surface, their role may seem minimal, its underlying importance has been acknowledged as imperative across various industries, including the automotive space. As vehicles become increasingly software-defined, with functions controlled and updated via internet demand for a secure infrastructure.
The role cryptographic keys in Public Key Infrastructure (PKI) of vehicles exactly serves the requirement. It facilitates communication between ECUs enabling everyday automotive functions and reduces the attack surface of cyber vulnerabilities.
This guide aims to help you understand in depth; how cryptographic keys operate within automotive PKI and their management system.
Overview of Cryptographic Keys and Its Role in Automotive Ecosystem
The use of cryptographic keys dates to their establishment in military communication in ancient times. However, with significant advancements in technology, its modern applications extend its use to enhance digital security.
At its core, cryptographic keys are a combination of a string of bits of information with specialized algorithms.
In software-defined vehicles (SDV), the role of cryptographic keys is no less than that of an ignition key. Although it does not start the vehicle’s engine, rather, it acts as the backbone for every basic functionality used across modern vehicles, including:
- Securing boot authentication
- Encrypting ECU communication
- Ensuring protection during FOTA updates
Commonly, two types of keys are used in automotive applications: symmetric and asymmetric.
Symmetric keys are random numbers that use the same keys for both encryption and decryption.
Conversely, asymmetric keys utilize the Public Key Infrastructure (PKI), has a public and private key combination for digital signature generation and verification, as well as asymmetric encryption and decryption. Its application in vehicles extends to V2X communication, secure key exchanges, and authenticating OTA updates via digital signatures.
While both types of keys are critical for vehicle security, this guide primarily focuses on their application in a Public Key Infrastructure (PKI).
Automotive Key Lifecycle in PKI
Cryptographic keys in the Public Key Infrastructure plays a crucial role in the security of software-defined functionalities. Moreover, its usage extends throughout the lifecycle of a vehicle that demands for the need of proper storage, usage and maintenance.
Therefore, alongside the vehicle lifecycle runs the automotive key lifecycle that encompasses the entire journey of cryptographic keys from their generation to retirement.
The automotive key lifecycle not only helps maintain system integrity to secure the cryptographic keys but also ensures regulatory compliance and protects vehicles against evolving cybersecurity threats.
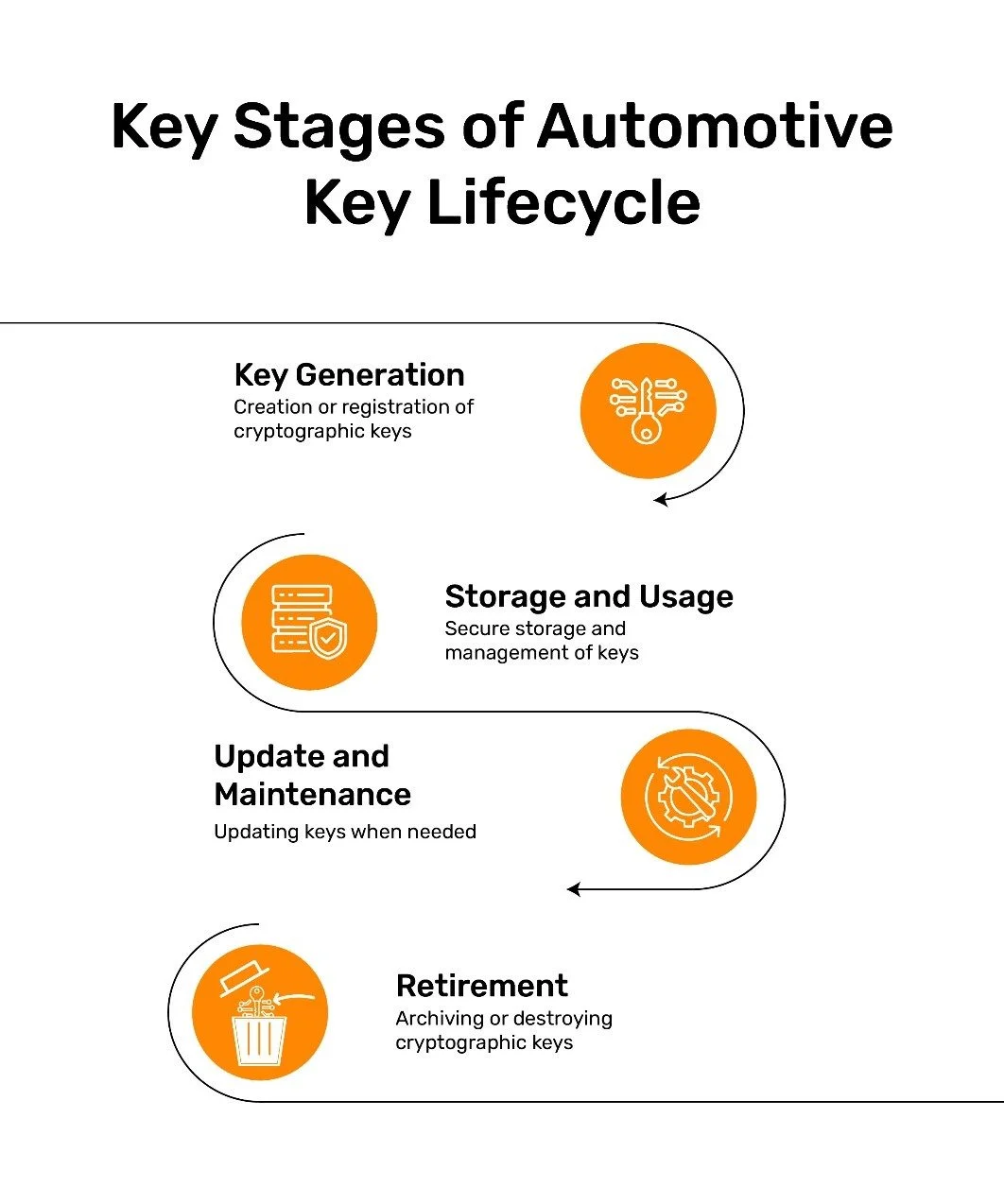
While the automotive key life cycle follows a step-by-step management procedure, it is broadly classified into four key stages, which include:
- Key Generation
- Storage and Usage
- Update and Maintenance
- Retirement
Key Generation
Key Storage and Usage
Key Update and Maintenance
Key Retirement
Key generation is the first stage, refers to the generation or registration of cryptographic keys in automotive systems. The process takes place within the secure backend of PKI systems operated by OEMs or Tier-1s and is then securely injected into the vehicle during manufacturing or provisioning.
For PKI systems, this primarily involves generating asymmetric key pairs (public/private) that are bound to specific vehicle components.
Once cryptographic keys are generated, the next step involves securely storing and managing them within the vehicle and across the backend infrastructure.
In the automotive ecosystem, Hardware Security Modules (HSMs) play a central role in this process. These modules securely generate root and intermediate keys, store them in a tamper-protected environment, and perform various cryptographic operations such as digitally signing firmware, certificates, and encrypting/decrypting sensitive data.
During manufacturing or provisioning, HSMs also facilitate secure key injection, reinforcing the trust chain within the Public Key Infrastructure (PKI) architecture.
Cryptographic keys, once deployed, need maintenance throughout the lifespan of the vehicle, which often exceeds ten to fifteen years. Over time, these keys may become vulnerable to evolving attack techniques or outdated algorithms. Regular key updates are therefore essential to preserve secure communication and system integrity.
Key updates are typically triggered when a key is suspected to be compromised via cyberattacks, side-channel exploitation, or supply chain issues, or when cryptographic standards evolve. While not always part of standard FOTA updates, key updates often accompany critical security patches to ensure continued protection of in-vehicle functions and backend interactions.
These practices help reduce the risk of unauthorized access, enable secure OTA functionality, and meet compliance requirements.
The prolonged use of cryptographic keys can increase the risk of compromise, especially as vehicles reach the end of their lifecycle. As a preventive security measure, cryptographic keys within the vehicle and in the backend PKI infrastructure are securely retired either through archival or destruction.
This process typically takes place when the vehicle is decommissioned, scrapped, or if a key compromise is suspected. Key retirement ensures that even after the vehicle is disposed of, the associated keys cannot be misused to gain unauthorized access.
Within the vehicle, this involves physically destroying the key stored in a chip, securely erasing it from storage, or wiping all traces of the key and related data. On the backend, keys that were generated and stored within HSMs is also securely deleted or marked as revoked, ensuring complete retirement across the entire PKI ecosystem.
What is a Key Management System?
By now, you might have a clear understanding of what the automotive key lifecycle is and the stages it passes through. Nevertheless, while the whole process deals with the lifecycle of keys within a vehicle, its overall security is ensured through a key management system.
What is VKMS and how is it Different from Other KMS
VKMS (Vehicle Key Management System) is essentially a domain-specific KMS designed for vehicle immobilizer and ECU communication keys. Many modern VKMS implementations are built on PKI principles, using asymmetric cryptography (public/private keys) to authenticate and authorize components.
A general KMS manages keys for many applications (databases, encryption, TLS, etc.). On the other hand, VKMS manages keys specifically for vehicles, and performs critical functions such as:
- Generating or retrieving vehicle-specific keys (e.g., immobilizer secret, rolling codes, symmetric session keys).
- Securely injecting the keys into ECUs.
- Updateing keys when components change (ECU replacement, key addition).
- Storing metadata (key IDs, validity, usage logs) in OEM backend servers.
Role of PKI Comes In VKMS
To make VKMS trustworthy, many OEMs use Public Key Infrastructure (PKI)
In PKI Every component (ECU, key, even the diagnostic tool) has a digital certificate tied to a private and public key pair. These certificates are signed by a trusted Certificate Authority (CA), in this case, the vehicle manufacturer’s backend. This helps devices authenticate each other using these certificates before exchanging any secret data.
In a VKMS , PKI ensures only genuine, manufacturer-approved ECUs and keys can join the vehicle network. Additionally, it also ensures key and immobilizer data can’t be cloned or injected by rogue tools and every operation is logged, timestamped, and linked to an authorized technician.
While this might sound technical let’s understand it with the example of a workshop where a technician just replaced a faulty engine ECU. Here’s what happens under the hood
- Tool Authentication: The workshop’s diagnostic tool connects to the OEM’s backend and proves its identity with a manufacturer-issued certificate (PKI).
- Session Authorization: The backend confirms the technician’s permissions and starts a secure VKMS session with a PKI-signed challenge and response.
- Key Material Distribution: The backend generates or retrieves the correct immobilizer keys, encrypts them, and sends them to the tool.
- Programming: The tool injects the new key material into the replaced ECU and re-aligns it with the immobilizer and other modules.
- Verification: All components confirm they trust each other, using digital signatures, and the car is ready to start.
FAQ
Key management in automotive cybersecurity deals with the secure handling of cryptographic keys throughout the entire automotive key lifecycle to ensure safe and secure vehicle communications and prevent unauthorized access or data breaches.
Cryptographic keys in ECUs are used to authenticate software, secure communication between components, and protect stored data. They enable secure boot, firmware updates, and encrypted diagnostics. These keys are typically stored in Hardware Security Modules (HSMs) to prevent unauthorized access or tampering.
During vehicle production, key injection entails safely creating and integrating cryptographic keys into ECUs or secure modules (such as HSM or TEE) to guarantee that every part of the vehicle can securely communicate with the others.
PKI is used to secure OTA updates by utilizing a private key to sign firmware. To ensure authenticity and stop harmful or unauthorized code from being deployed. The update is digitally signed by the OEM using a private key. The vehicle uses the corresponding public key to verify the signature and ensure the update’s authenticity and integrity before installation.
OEMs must use secure key lifecycle management, which includes appropriate key generation, storage, usage, updates, and revocation, while guaranteeing traceability and compliance with UN Regulation No. 155 (Cybersecurity and Cybersecurity Management System) and UN Regulation No. 156 (Software Updates and Software Update Management System)
Automotive PKI manages digital certificates and public/private key pairs to establish trust, mainly for secure OTA updates and V2X communication. Key Management Systems (KMS) handle the full lifecycle of both symmetric and asymmetric keys from generation to revocation. PKI provides identity verification and trust using certificates issued by trusted authorities. KMS ensures secure and efficient use of keys within the vehicle, especially for ECU-to-ECU communication like SecOC. While PKI builds external trust, KMS supports internal key operations; both work together to secure the vehicle ecosystem.
The lifecycle of vehicle key management begins with the cryptographic key generation, its usage and storage, maintenance and updating, and ends at retirement when the vehicle is disposed of.
Connected cars often use symmetric algorithms like AES for fast, secure internal communication while asymmetric algorithms like RSA and ECC are used for securing communication between PKI and V2X.
Wrapping Up
With vehicles rolling computers, security breaches are no longer just about stealing the car. They are about remote hijacking, disabling safety systems, or tampering with OTA (over-the-air) updates.
A well-implemented VKMS, backed by PKI:
- Keeps vehicle security intact after service.
- Prevents cloned or counterfeit ECUs from being accepted.
- Integrates with OTA signing, ensuring even post-sale updates are secure.
- Scales globally, managing unique keys for millions of vehicles without losing track.
To get a clear understanding of how it may help you, make sure you check out our case study where we assisted a top automaker in overcoming inefficiencies in ECU access and token production: Public Key Infrastructure Solution for Secure & Efficient ECU Token Management


