The emergence of the Internet of Things (IoT) has revolutionized the way in which businesses operate in the new industrial era. IoT is at the helm of rapid growth, with the global market for IoT end-user solutions predicted to reach 1.6 trillion US dollars by 2025.
In this context, the topic of IoT security is of great interest to product designers, manufacturers and procurement personnel across industries. As the number of connected devices grows, the volume of data to be protected and complexity of Internet of Things security also increases.
How can you secure your Internet of Things ecosystem to be immune to severe security breaches? – This is the question being enthusiastically discussed in the industry circles today. Our in-house IoT experts believe that a holistic approach to Internet of Things security is the way forward.
This is the first in a three-part series of blogs that discusses the holistic security approach and ways in which full-stack IoT security can be achieved.
Full Stack IoT Cybersecurity
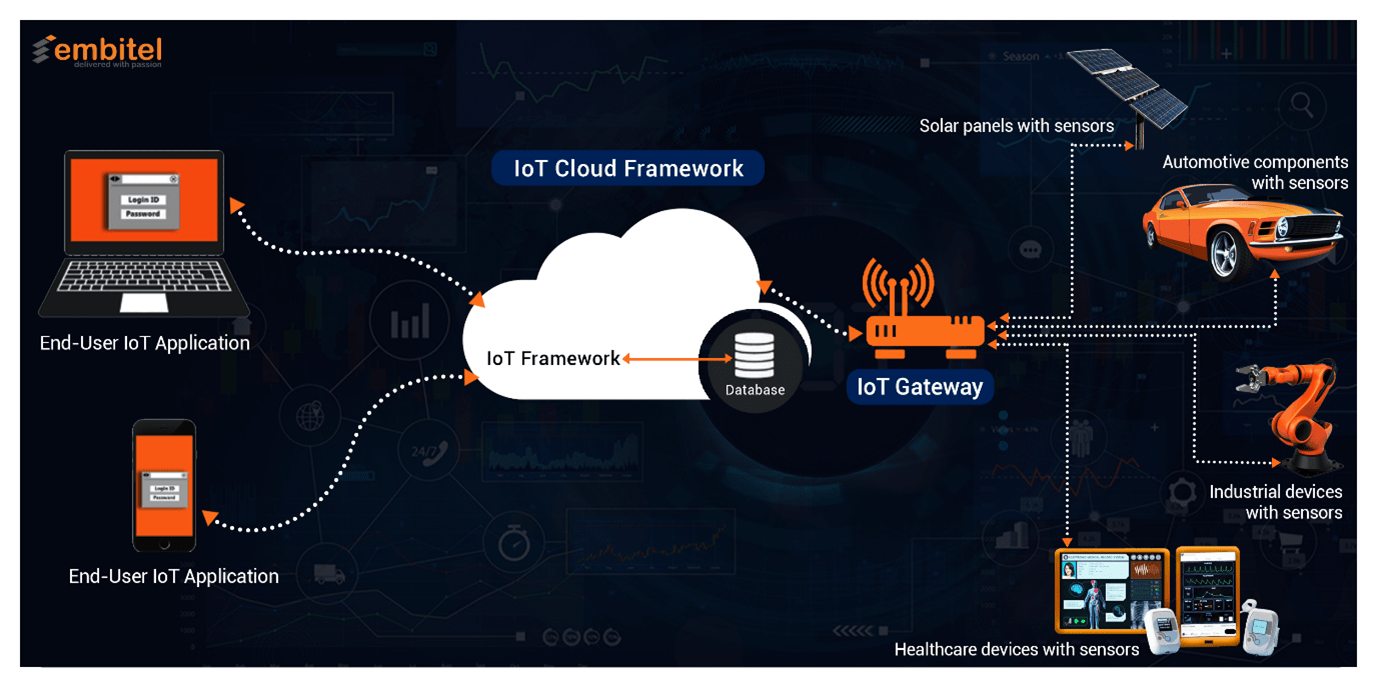
When developing a secure end-to-end IoT ecosystem, it is crucial to ensure that security protocols are adhered to at each layer of the infrastructure. In the image below, we have highlighted the various layers of a full-stack IoT solution:
- The end-user application layer
- IoT cloud framework
- IoT gateway layer
- Devices with IoT sensors
- IoT connectivity (PAN/WAN)
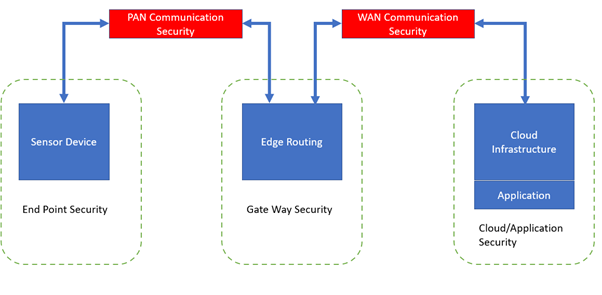
Holistic IoT security should encompass methodologies to ensure:
- End Point Security at the level of the Device Sensor
- Gateway Security that constitutes Edge Routing
- Cloud and Application Security
- PAN and WAN Communication Security at the connectivity level
End Point IoT Security Elements
End point security encompasses all the protocols that should be followed to ensure that there are no security violations at the IoT device level. The primary areas of focus are IoT cybersecurity at:
- Device hardware/software level
- Bluetooth PAN level
IoT device security (Hardware and Software level) – IoT device manufacturers have been increasingly incorporating security features in the device hardware and software to offer a primary layer of protection.
Key IoT security features that can be integrated at this level include:
- Physical and Tamper Security – Each connected device in an IoT infrastructure can be a potential entry point to access the entire network or the confidential data handled within. For security to be completely realized in an IoT infrastructure, it should be incorporated in the devices during the design and build phases.
The IoT devices should be able to authorize their identity, encrypt their data, and protect data that is stored locally.
Physical security is an important aspect as well.
- Devices should be designed to offer tamper resistance so that it is difficult to extract sensitive information by unauthorized personnel.
- Devices can be located in unattended or private areas to limit physical access. Chips that manage crucial functionalities of a device can be removed by attackers. To prevent this, these chips can be configured in a way that they get destroyed during the unauthorized removal process.
- Special attention should also be given to the device casing. As a safety measure, it is possible to program the device to get permanently disabled on opening the case by unauthorized personnel.
- Secure Boot and Root of Trust – A hardware Root of Trust is the security foundation for an SoC, electronic system or any other semiconductor device. It consists of the keys for cryptographic functions.
Hardware Root of Trust can be categorized into fixed function and programmable categories.
- Fixed function – A fixed function root of trust is a simple and small state machine that performs few static functions like certificate validation, data encryption, key management, etc.
- Programmable – A programmable root of trust has a CPU that performs all the functions of the fixed function root of trust and many more complex security functions. Since it is upgradable, it can be programmed to execute new cryptographic algorithms that protect from the dynamic and ever-evolving threat landscape.
Root of Trust also enables the secure boot process of the device. Secure Boot is a mechanism that uses public key cryptography to ensure that the software components have been digitally signed and unmodified while the system boots.
Root of Trust is based on a hardware-validated process of booting. When we combine this with the Secure Boot process that validates software integrity, the security loopholes that can be exploited are not easily accessible to hackers.
- ASLR – Address Space Layout Randomization (ASLR) is a memory protection technique for operating systems that uses randomization for avoiding attacks related to memory corruption, code injection, code reuse and buffer overflow.
- Guard Band in OS – A guard band offers insulation between signals in wireless data communication and is hence, effective in preventing interferences.
- Chip Security – A strong IoT security architecture begins at the chip level. The basic assets of a chip include cryptographic keys that safeguard data and authenticate devices in the network. Chip manufacturers have been introducing advanced security functions in chips that can form the foundation of secure IoT devices.
- TPM/HSM – Trusted Platform Module (TPM) is a hardware security solution that provides isolation of private keys. It also enables secure generation of cryptographic keys and random number generation. A Hardware Security Module (HSM) is a physically separate chip (in the form of a plug-in card or external device) that safeguards digital keys for crypto processing and authentication. HSM is also a more cost-effective solution when compared to TSM.
- Disable Debug Access – Disabling the debug interface, enabling Flash Security and disabling FLASH Mass Erase prevent the unauthorized reverse engineering of code on an IoT device.
Bluetooth PAN level security – This includes the following security considerations:
- Device Authentication and Device Identity – When a large number of devices are connected to an IoT network, strong device authentication processes need to be in place. Each IoT device is assigned a unique identity that is evaluated when the device tries to connect to the server directly or through a gateway.
Administrators also find the unique ID useful for tracking and managing devices throughout their life cycles. - Beacon Shuffling – Bluetooth beacons are vulnerable to attack by malicious parties. If a hacker has access to your beacons’ Majors, Minors, UUIDs and MAC addresses, your devices can be easily spoofed. The IoT infrastructure would then consider the clones as authorized devices.
Beacon shuffling is a great way to prevent a cloning attack. Shuffling the identifiers on a daily or weekly basis modifies the Majors and Minors of the beacons randomly, and hence, prevents device spoofing.
Apart from the above measures, optimizing radio strength and disabling unused protocols in the Bluetooth stack can also help in reinforcing Bluetooth PAN level security.
Summary
We now have an idea of the various measures that can be implemented to ensure IoT security at the connected device (hardware and software) level and the Bluetooth PAN level. We will deep dive into IoT Gateway security in Part 2 of this blog series. Stay tuned!
Other articles in this blog series:
IoT Security – Part 2 of 3: Analysis of IoT Gateway Security
IoT Security – Part 3 of 3: IoT Cloud Security and IoT Application Security


