In part 1 of this blog series Principles of Holistic Security and End Point Security Elements, we introduced to you the basic components of an IoT infrastructure. We also explored holistic IoT security principles and how end point security can be implemented at the IoT device level.
In this blog, we will look at the different components of IoT gateway security to protect IoT gateway devices in the infrastructure.
IoT Gateway Security
The IoT gateway is basically a bridge between the devices with sensors and the cloud. IoT gateway solutions may also offer local processing and storage capabilities. Additionally, gateway devices can control field-deployed IoT devices based on the sensor input data.
Since an Edge Gateway is located between the local intranet and external internet, it is a critical point for network connectivity. The gateway also has higher processing power than field-deployed IoT controllers (retrofitted with sensors). This implies that the gateway has superior software that, in turn, is vulnerable for hackers to exploit. Hence, it is crucial that the gateway is adequately protected.

IoT gateway security includes the incorporation of security features at multiple layers. Let us take a look at these in detail:
- Device hardware/software level
- Bluetooth PAN level
- WAN level security
IoT device security (Gateway hardware/software level)
The hardware and software security measures for a gateway device are similar to that for the IoT sensor devices. We have explained this in part 1 of this blog series; so we will not go into the details here.
Here is an overview of IoT gateway security elements at the hardware and software level.
- Physical and Tamper security
- Secure Boot and Root of Trust
- ASLR
- Guard band in OS
- TPM/HSM
- Chip Security
- Disable debug access
Bluetooth Personal Area Network (PAN) level security
As far as PAN level security is concerned, there are several security components that can be incorporated in the system:
- Access Control Models – Access control models for an IoT environment are usually classified according to the basis for access control. Hence, you can have Role-based access control, Usage control, Attribute-based access control, Capability-based access control or Organizational-based access control models, to name a few. These models ensure that there is easy identification to enable execution of tasks permitted for each entity/user.
- Blacklisting/Whitelisting of Bluetooth MAC Addresses – It is possible to create a list of denied/allowed wireless clients that can connect to the device based on their MAC addresses. MAC addresses that are included in the whitelist will have access to the device, and all other clients are denied the access. Conversely, MAC addresses in the blacklist will not have access to the device, while all other clients are allowed access.
- Firmware Update Administration – Whenever there is a firmware update on the gateway device, there should be strong authentication mechanisms. Ideally, the firmware update should be cryptographically signed, and the gateway should be able to verify the signature before the firmware update process.
- Logging and Usage Meters – IoT data can be effectively managed and used by organizations for generating security intelligence through Artificial Intelligence (AI) technology. Data can be easily collected, organized and processed through logging or usage meters. Device logs will provide information such as connections, errors and other such lifecycle events. The results gained from this raw data can be utilized for reinforcing the security of the IoT ecosystem.
- Control Pairing/Bonding – BLE pairing is the process in which temporary keys will be found and exchanged with a Bluetooth device. This temporary key encrypts the connection and maintains it for a short period of time. BLE bonding refers to the establishment of a long-term connection with another device. The devices would have exchanged long-term encryption keys and during the pairing process, these keys are utilised. Hence, the devices do not have to generate new encryption keys at the time of each connection.
Bluetooth Security of IoT devices encompass multiple security modes and security levels. Security during the pairing and bonding processes includes three phases:
- Phase 1 (Pairing) – Capability exchange
- Phase 2 (Pairing) – Secure key generation
- Phase 3 (Bonding) – Transport specific key distribution
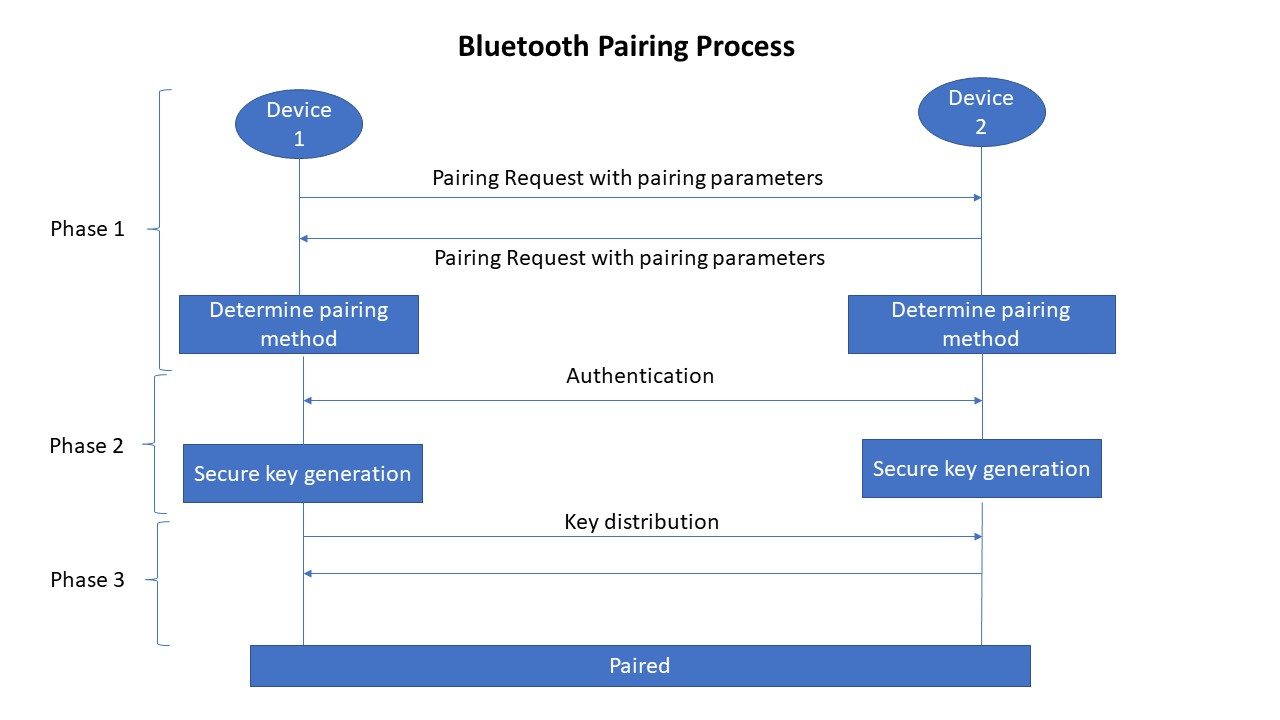
|
Bluetooth Passkey Entry is a method to ensure that security risks are mitigated at the time of device pairing (Phase 2). However, this method has a few limitations. As of Bluetooth 4.2, the LE Secure Connections pairing process reduces most of the limitations involved in the pairing process using passkeys. Other methods for mitigating security risks while pairing are Numeric Comparison, Just Works and Out of Band Legacy pairing. |
Wide Area Network (WAN) level security
IoT gateway security elements at the WAN level include the following:
- Firewalls – An IoT firewall can be deployed in the network to protect the system against several security threats:
- Network threats – The firewall is capable of preventing DDoS and application layer security breaches.
- Abuse of service – IoT devices (including gateways) are protected from being used unexpectedly, without authorization.
- Device threats – The firewall ensures that the devices in the IoT network are connected only with known and safe locations.
Usually, the administrator of the network configures the firewall setting by defining the destination IP addresses, IP networks, destination protocols, ports or host/domain names that are permitted in the network.
- Port Lockdown – In each IoT device, disabling the open external ports can protect the hardware and the data within. IoT Security attacks such as fuzzing, buffer overflow, DoS attacks, etc. can be prevented in this manner.
- Software-Defined Perimeter (SDP) Interface – Software-defined perimeter is a security framework that manages access to IoT resources based on identity. It works on the principle of hiding crucial assets within an opaque cloud that is inaccessible to outsiders. The hidden assets may also be on premises, in a perimeter network, data center server or an application server. The SDP interface acts as a broker between the protected applications and users who are allowed access on fulfilling the validation criteria. Essentially, SDP forms an invisible screen that protects IoT components against cyberattacks, malware and other such security breaches.
IoT gateway security (WAN level) can also be ascertained in several other ways. This includes maintaining Access control lists and Blacklisting/Whitelisting MAC addresses.
Summary
Now we have a fair idea of the various measures one can take for ensuring IoT gateway security in an Internet of Things infrastructure. In the next part of this blog series, we explore the IoT cloud security and IoT application security aspects along with communication security.
Other articles in this blog series:
IoT Security – Part 1 of 3: Principles of Holistic Security and End Point Security Elements
IoT Security – Part 3 of 3: IoT Cloud Security and IoT Application Security


