Imagine it is 2 a.m., and your car, connected to the cloud, silently accepts an “auto-update.” By morning, you notice the car behaving erratically or the cabin microphone recording unexpectedly, or the vehicle refusing to start.
What went wrong? The update package contained a malicious file, allowing an attacker to install malicious firmware and potentially compromise your car.
Sounds like a fictional thriller. Right?
But as modern automobiles advance, their features are becoming increasingly software oriented. Every ECU, sensor, and digital service in vehicles today is software-driven, and OTA updates are the lifeline that keeps them up and running.
This article will dive into sophisticated security threats to OTA updates and the role of Trusted Applications, the core that secures the mechanism in modern vehicles.
What are Automotive OTA Updates? Its Relationship with Trusted Applications?
Over-the-Air (OTA) updates are wireless software distribution mechanism that enables OEMs to remotely push system enhancements in vehicle’s ECUs remotely.
Rather than requiring physical access vehicles, it allows automakers to remotely deliver software patches, feature enhancements, and security fixe. This mechanism leverages cellular or Wi-Fi connectivity that transmits signed update packages from a centralized cloud backend to the target vehicle.
Nevertheless, this convenience comes with inherent risk making the wireless transmission prone to malicious and foreign attacks.
To counter these threats, OEMs rely on a multi-layered apparatus comprising secure boot mechanisms, encrypted communication, access control, and intrusion detection systems (IDS). Each layer ensures that only trusted entities can initiate or modify the software update process.
At the core of this defence, lies the Trusted Applications (TAs) operating within a Trusted Execution Environment (TEE) act as the vehicle’s digital gatekeeper. These secure applications ensure that only firmware verified with authentic cryptographic signatures is installed on the ECUs, maintaining the integrity and authenticity of every OTA update.
Security Challenges in OTA Update
OTA updates form the backbone of continuous software evolution in software-defined vehicles. They do not depend on external services to add additional functionalities; OTA updates play their role end-to-end, from patching vulnerabilities to deploying new features across fleets.
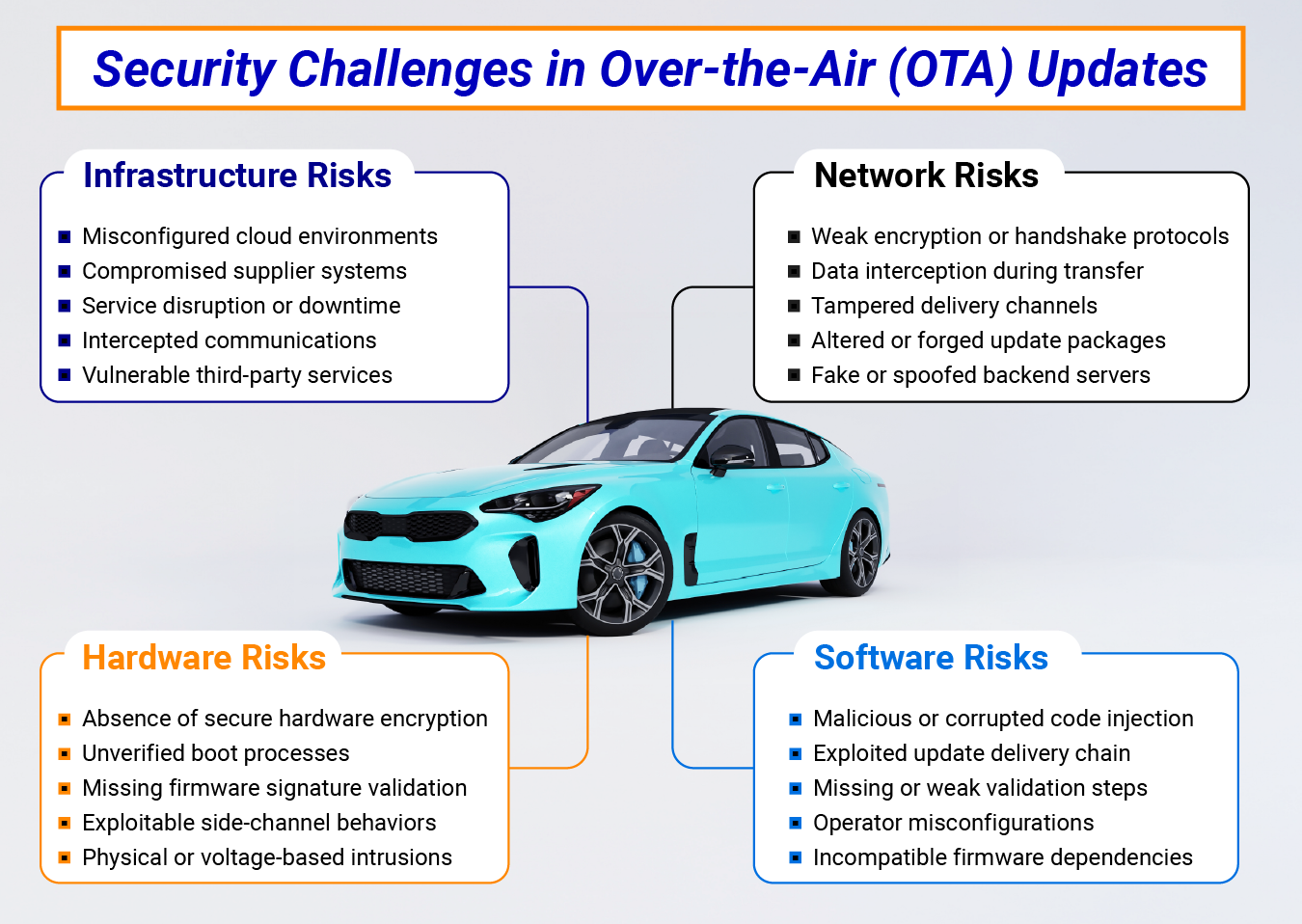
However, this same capability also expands the attack surface across multiple layers of the vehicle software stack. This can basically occur at four different layers:
- Infrastructure Layer
- Network Layer
- Software Layer
- Hardware Layer
- Infrastructure Layer Challenges
- Network Layer Challenges
- Software Layer Challenges
- Hardware Layer Challenges
The most fundamental challenges arise at the backend infrastructure layer, where OTA delivery pipelines span multiple cloud instances, CI/CD environments, and edge distribution nodes.
Misconfigurations or insufficient hardening at any stage of this pipeline can allow attackers to gain unauthorized access, manipulate firmware binaries, or inject malicious payloads into legitimate update containers. Moreover, compromised signing servers or insecure build environments create opportunities for supply chain attacks where malicious firmware is cryptographically “trusted” by design.
At the network layer, the reliance on heterogeneous communication channels such as cellular, Wi-Fi, or V2X introduces further complexity. Weak or outdated transport encryption, unvalidated certificates, or improper session key handling can expose update packages to interception or replay attacks.
Moreover, man-in-the-middle (MITM) attempts can alter metadata, inject malicious fragments, or even force partial updates, leading to inconsistent ECU states and potential denial-of-service conditions.
The software layer itself presents additional risks. Vulnerabilities in update agents, verification routines, or rollback mechanisms can be exploited to bypass integrity checks or trigger unauthorized firmware installations.
In addition, attackers also attempt to exploit misconfigured signature validation logic, for instance, by accepting unsigned delta updates or skipping verification during error states. Equally concerning are rollback attacks, where older, vulnerable firmware versions are reinstalled intentionally to exploit known weaknesses.
At the hardware level, the challenge intensifies. Legacy ECUs often lack hardware-backed cryptographic accelerators or Trusted Platform Modules (TPMs) necessary to enforce secure boot and signature verification. In such systems, firmware authenticity is dependent entirely on software-based validation, which is susceptible to fault injection or side-channel attacks. Extracted private keys or signature verification bypasses at this level can compromise the integrity of the entire OTA chain.
What is Trusted Execution Environment (TEE) in Automotive Systems?
Now that it is evident how vulnerabilities can appear at every layer of the OTA update pipeline, it becomes clear that securing the software itself isn’t enough. The validation process, where firmware is decrypted, verified, and installed, must happen in a space isolated from the rest of the system.
This is where the Trusted Execution Environment (TEE) comes into play.
In simple words, the TEE is a secure area within the main processor, designed to execute sensitive operations like key management, decryption, and signature verification in isolation from the vehicle’s regular operating system. Even if the primary OS or application layer in a vehicle is compromised, the TEE remains protected and uncompromised.
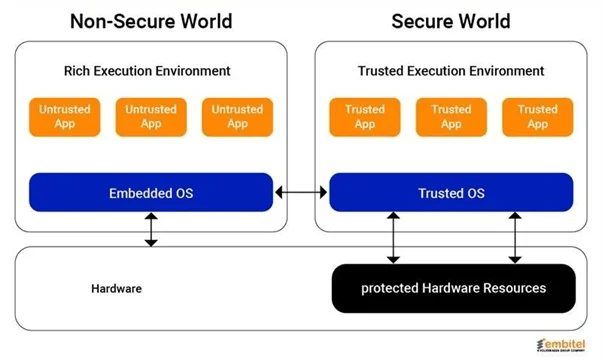
Within the modern automotive environment, this separation is crucial. Basically, the TEE runs alongside the Rich Execution Environment (REE), aka the main OS that handles infotainment, connectivity, and other user-facing functions. However, it operates independently with restricted access, although the REE can request certain operations from the TEE, but it cannot view or manipulate what happens inside it.
In practice, this hardware-backed isolation keeps critical security functions, such as verifying the authenticity of update containers or decrypting firmware, far from potential malware or unauthorized code.
For example, when an OTA update arrives, the TEE performs a multi-step validation:
- Step 1: Verifies the digital signature to confirm that the firmware originates from a trusted OEM source.
- Decrypts the update container using a secure key stored only within the TEE.
- Step 3: Authorizes installation only after these validations succeed, preventing tampered or forged updates from executing.
This mechanism, combined with hardware-based cryptographic protection, forms the foundation of in-vehicle security. However, the true intelligence of this process lies in the software entities running inside the TEE known as Trusted Applications (TAs).
Trusted Application and its Role in OTA Update Process
While the Trusted Execution Environment (TEE) provides the secure foundation, it is the Trusted Applications (TAs) within it that actively enforce security policies and validate each step of the update process.
Think of the TEE as a secure vault and the TAs as the guards inside it, responsible for verifying who gets access, what data can enter, and what actions can be performed.
During an OTA update, the TA plays a pivotal role in ensuring that only authenticated and authorized firmware is installed on the Electronic Control Units (ECUs).
Architecture and Workflow of Trusted Application (TA)
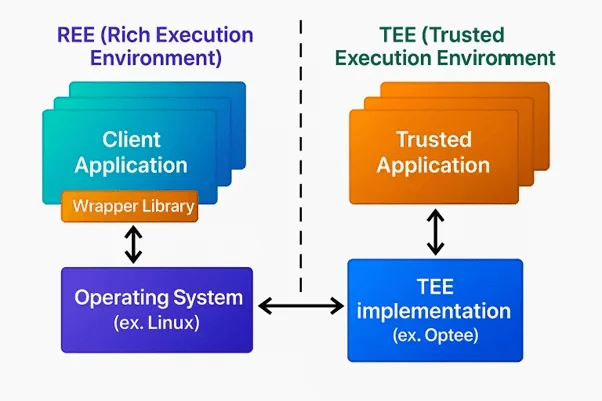
The architecture of a TA typically consists of three critical layer that together enable secure operation:
- Client Interface (Enables REE and TEE Communication)
- Trusted Core Logic (That executes within TEE)
- Secure Storage and Key Management Layer
In the first layer, the REE communicates with the TEE via a standardized API, often defined by the GlobalPlatform TEE Client API. This communication follows a request-response model where the REE acts as a client calling for specific secure functions (signature verification or decryption).
Next, the trusted core logic executes within the TEE. This is the core of the TA, where actual cryptographic operations, verification routines, and access controls are executed. The logic is implemented using secure APIs (TEE Internal Core API) that provide cryptographic primitives, secure storage access, and session management. These operations occur in complete isolation, separate from external tampering or inspection.
Lastly, TAs rely on hardware-backed secure storage, often tied to a Hardware Root of Trust (HRoT) or embedded HSM within the SoC. This layer securely holds cryptographic keys, certificates, and policy data, ensuring that even if the main OS or storage medium is compromised, these keys remain protected.
Workflow of TA During OTA Update
During an OTA update, the TA follows a structured validation sequence to guarantee software integrity and authenticity:
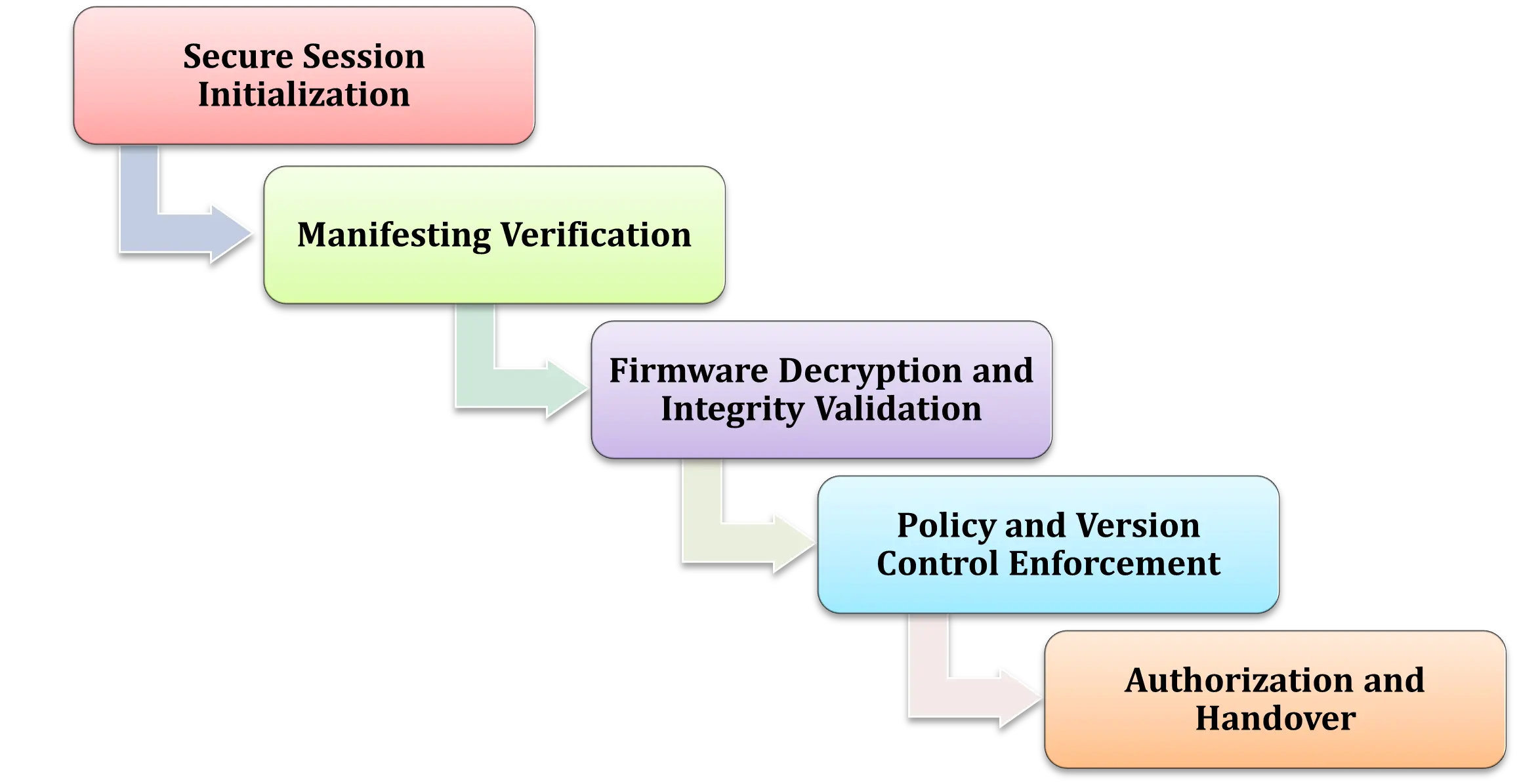
Secure Session Initialization
The REE initiates a secure session with the TA, sending metadata and encrypted update information. The TEE validates the request origin before processing.
Manifesting Verification
The TA verifies the update manifest using OEM-trusted public keys stored securely within the TEE. This ensures that the update package originates from a legitimate source.
Firmware Decryption and Integrity Validation
The TA decrypts the firmware image using private keys stored in the TEE and validates its integrity via cryptographic hash verification.
Policy and Version Control Enforcement
Before authorization, the TA checks update policies, firmware version, and rollback prevention logic—ensuring that outdated or unauthorized versions cannot be installed.
Authorization and Handover
Upon successful validation, the TA generates an authorization token that allows the REE to proceed with ECU installation. The REE cannot bypass or manipulate this approval mechanism.
Why Trusted Applications Are Central to Secure Automotive Software?
While the TEE provides the foundation for secure operations, Trusted Applications (TAs) serve as the enforcer of trust within automotive systems. Their role extends beyond validating OTA update packages; they form the operational layer that keeps the in-vehicle software ecosystem authentic, reliable, and tamper-proof.
Acts as the Enforcer of Digital Trust
SDVs comprise dozens of ECUs exchanging commands and data in real time; TAs ensure that only authenticated software and approved commands can execute. They enforce cryptographic policies, verify digital signatures, and act as the gatekeepers of every secure transaction inside the vehicle.
For instance, when the infotainment ECU requests an update or communicates with the central gateway, the TA validates the source, checks for authorization, and verifies integrity before allowing any action to proceed. This enforcement mechanism ensures that no unverified command, malicious firmware, or unauthorized diagnostic request can compromise system integrity.
Secure Key Handling and Isolation
Cryptographic keys secure every operation, and their management determines the overall resilience of the vehicle system. Trusted Applications helps in the overall management of these keys within the confines of the TEE, ensuring they are never exposed to the Rich Execution Environment (REE) or vulnerable application layers.
Continuous Protection
Security is a continuous process that constantly runs even after an update is verified and installed. Trusted applications also play the role of realtime monitoring and perform regular runtime integrity checks, verify security configurations, and prevent unauthorized access to protected memory regions.
For example, if a malicious process attempts to alter firmware memory or execute privileged functions through backdoors, the TA detects and blocks the request before it reaches execution level. This persistent validation ensures that vehicle software remains trustworthy across its entire lifecycle.
Regulatory Compliance and Traceability
Automotive cybersecurity is not just a technical concern anymore it’s a regulatory requirement. With global standards like ISO/SAE 21434 and UNECE WP.29, OEMs are now accountable for ensuring end-to-end software integrity and update security.
TAs inherently adhere to compliance by maintaining verifiable audit trails, enforcing secure key usage, and validating update authenticity at every stage. Their presence allows OEMs to demonstrate that critical security functions are isolated, traceable, and policy-driven, fulfilling both compliance and operational assurance in one framework.
Conclusion
The automotive industry is rapidly transitioning towards centralized compute and zonal architectures. This undoubtedly increases their reliance on Trusted Applications that is assumed to will exponentially.
Future ECUs won’t just manage isolated domains; they’ll coordinate multiple vehicle zones, requiring secure orchestration at scale. TAs will evolve into modular security controllers, capable of:
- Verifying and authorizing inter-domain communication,
- Managing distributed credentials, and
- Enforcing security policies dynamically across the vehicle network.


