This is the era of connectivity! And cars are not behind. To enable connected car technologies like telematics, a vehicle houses a gamut of software systems communicating not only with each other but with external systems too. Automotive diagnostics is one such activity that is performed between the vehicle ECUs and external testing devices. Needless to mention, DoIP (ISO 13400) is the superhero that makes this remote diagnostics possible.
As the communication takes place over the internet, there are fair chances that an ECU system can get hacked. There are external networks at play and a plethora of software services utilizing DoIP, all of which amplifies the risk of car network and ECUs being compromised.
A lot of security threats can emerge in the instance of a breach. For instance, when a car repair guy connects to a vehicle for diagnosis, how does he make sure he is connected to the right vehicle? How does OEMs ensure that the software update patch is not tampered with, before installation? There are several such security related questions that arise with DoIP. In order to rectify it, we must first understand the risks involved.
In this blog, we will analyse the DoIP software stack, from a security standpoint. We will also talk about the possible solutions and ongoing research in this area.
But before delving further into the topic, let’s spend some time in understanding remote vehicle diagnostics.
A Brief Background of Remote Automotive Diagnostics
Vehicle Diagnostics in Automotive Industry refers to examination of the car to resolve the fault (if any) and ensure seamless operations of all the software, hardware and mechanical systems.
Similar to how a pathologist tests the human body, by examining some parameters, to know about its health, automotive engineers and mechanics also examine certain vehicle parameters.
Usually, a manual vehicle diagnosis is performed by plugging in a tester device into an OBD port of the vehicle. This port provides access to the vehicle network, over which the diagnostics messages are sent and received.
However such on-site vehicle diagnostics is not always a feasible option.
To counter this, OEMs started to equip some high-end vehicles with capabilities to be diagnosed over-the-air. What started with brands-specific feature soon became standardization that we now know as DoIP!
This Standardization of technology has brought about cost reduction and ease of operations for all the stakeholders.
Before we proceed further to analyse DoIP from a security standpoint, it is important that we understand the DoIP communication scenarios and types of possible attacks.
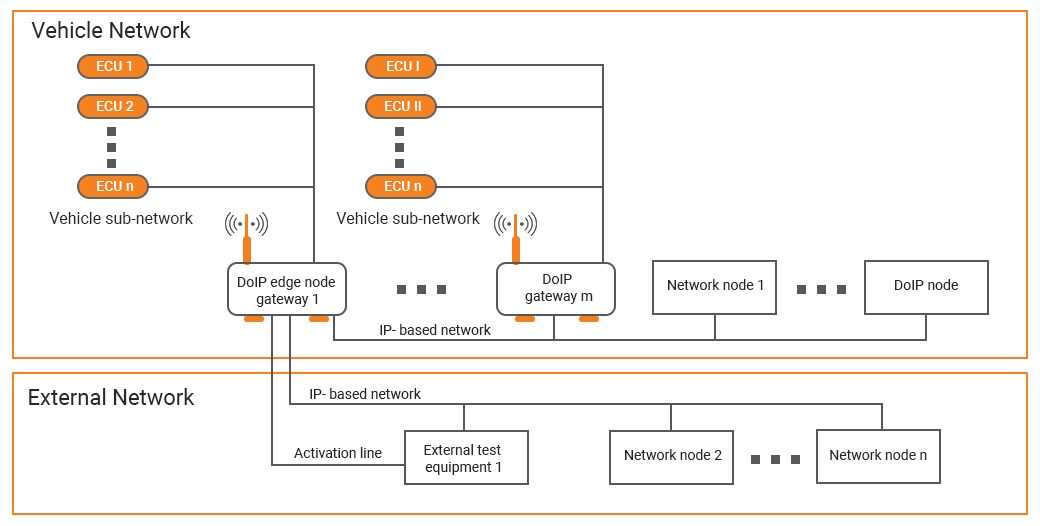
A Closer View of DoIP Communication Scenarios and Security Requirements
Attacks on DoIP based communication can be classified into Active and Passive attacks. Passive attackers do not try to alter the communication or interfere with it. They eavesdrop on the communication and steal vehicle information which may be put to various dangerous uses. An active attack, on the other hand, is a more participative one. The attackers might modify the information being sent on the network. They can completely delete the message or remove parts of it. They may also add certain unwanted messages into the stream. One can imagine how hazardous such activities might prove to be for a vehicle and its occupants.
Another aspect related to DoIP security is the communication scenario between the vehicle and the external testing device. Security threat increases manifold when communication occurs over unsecure external networks such as repair garage network.
- 1st Scenario- Physical Connection between vehicle and diagnostic tester: This is the safest application of diagnostics over physical ethernet. As the tester tool is directly connected to the vehicle ECU, there is almost no chance of eavesdropping or an external security threat. However, remote vehicle diagnostics is not possible with such a direct setup; this scenario is not useful for us in the context of DoIP.
- 2nd Scenario- Connection between vehicle and tester over a network: In this scenario, a vehicle is connected to a testing device over TCP/IP. The repair garage’s network may be an unsecure one and a hacker can use this threat vector to gain access to any of the vehicles connected to the network. Measures must be implemented that enable the tester to identify the right vehicle and the vehicle must also be able to reject multiple connection requests.
- 3rd Scenario- Connection between multiple vehicles and a tester tool: This is a little more complicated scenario where one tester tool caters to several vehicles using socket connection. However, each vehicle must be taking only one connection. A hacker can take advantage of such situation and control multiple vehicles by bouncing off the connection. DoIP protocol can be equipped with encryption algorithms to ward off such threats.
- 4th Scenario- Connection between one vehicle and multiple test devices or many test applications on a single tool: This is a highly advanced setup where a vehicle can accept diagnostics request from multiple tester devices or multiple test applications on one device. Such a scenario brings forward the chances of the attacker interfering with the working of multiple diagnostics devices.
Engineers integrating DoIP with vehicle ECUs are well aware of such threats and implement security measures to thwart all possible attacks.
Analysis of DoIP Software Services from security view-point
In this section, we will analyze some software services and technologies which are critical from the point-of-view of system security. These services facilitate in setting up the communication between entities in DoIP.
-
- Dynamic Host Configuration Protocol (DHCP): What does this software service facilitate? – It provides the IP address and other configuration details to the IP host that wishes to connect to the network.
Why is it sensitive from security point-of-view? – It is possible for hackers to exhaust all the available IP addresses by spoofing messages to the network. Due to this when a genuine host seeks connection, there are no IP addresses available and the service is denied to it. This is very common attack called the starvation attack.
In a different kind of attack, the hacker can present itself as the default gateway and answer to the DHCP requests from legitimate users. This can enable the hacker to send wrong diagnostics information about your vehicle.
-
- Internet Protocol (IP):What does this software service facilitate? – This service is responsible for relaying the data packets to the receiver. The sender and receiver are identified by the IP address. It is essentially the method or the protocol using which the datagrams are sent over the network.
Why is it sensitive from security point-of-view? – Automobile Hackers can take control of the network and fill the IP data fields with undesirable and wrong data. This can lead to serious issues in the functioning of the vehicle diagnostics system.
- Transmission Control Protocol (TCP):What does this software service facilitate? – The Internet Protocol delivers the data packets to the host but TCP is responsible for putting the packets in correct order. TCP is a correction-oriented protocol and therefore, it keeps track of the sequence of the packets.
Why is it sensitive from security point-of-view? – Hackers can execute a session hijacking attack with the objective of service denial and stealing of information. It is done by taking over a TCP stream or by inserting a RESET segment. Doing so forces a shutdown and hence, denial of service.
In a different kind of attack, the hacker can present itself as the default gateway and answer to the DHCP requests from legitimate users. This can enable the hacker to send wrong diagnostics information about your vehicle.
Having discussed about the possible vulnerabilities regarding the DoIP stack, we will now focus on the necessary preventive measures.
There are certain very critical best-practices, that as an embedded automotive engineer, one should aim to integrate seamlessly with the software design & development processes.
The security related best-practices ensure that one is able to deliver a robust DoIP Software Solution for an Automotive Project.
Best Practices to ensure security of a DoIP network
In order to secure the DoIP network, there are two important aspects to be taken care of: Communication security and Environment security.
The communication network over which the DoIP messages transmit can be secured by deploying tunneling technologies. In addition, clarity on how the system should be designed to manage the identity of the host and the nodes is required.
Securing the environment is achieved when the network endpoints are safeguarded against unauthorized entry. The research work in this area is quite over whelming however, the findings need to be aligned to DoIP requirements.
List of critical best-practices:
- Physical security of servers, routers and switches should be ensured to prevent any unauthorized access.
- User access profiles should be maintained with properly defined rights to restrict any illicit wireless access.
- Audit logging needs to be enabled for the DHCP servers. In case of unusually high number of requests to DHCP, the logs can be monitored to prevent unauthorized access.
- Set of TCP/IP protocols like SSL (Secure Socket Layer), TLS (Transport Layer Security), and IP Security can be put in place to prevent attack through TCP/IP.
DoIP is undoubtedly a protocol poised to change how automotive diagnostics work. Since DoIP runs over the Internet Protocol, one needs to be extra cautious about the safety of the system.
However, with necessary security measures discussed above, these vulnerabilities can be taken care of. The DoIP protocol specification in itself has several security measures in place to keep the vehicle and the underlying network safe.