The moment a system is connected to a network, it becomes vulnerable to cyber-attack. The attack may or may not be a successful one, depending on how secure the network is.
We witness the news of website/email hacking or the hijacking of social media accounts umpteen times. Movies go a few steps further to showcase how a full-blown cyber-attack on a government installation would look like. That might look like a bit of exaggeration but theoretically, such attacks are possible.
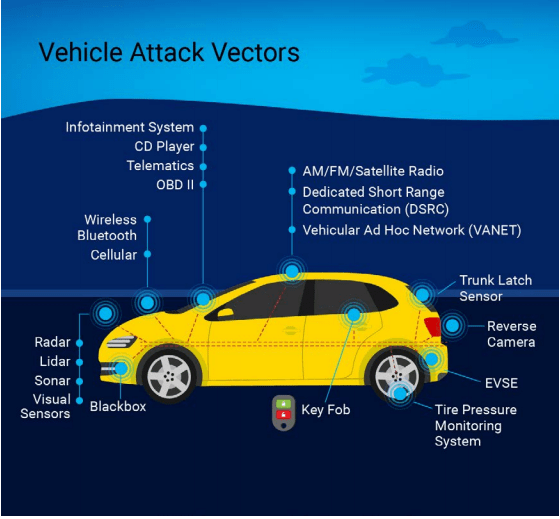
Now, that automobiles have also joined the digital bandwagon, the security threat has become real for them too. For example, a connected car is akin to a computer on a network with exposed interfaces such as steering, braking and other vital information about the occupants. A hacker can interfere with the vehicle systems or steal sensitive data if he gets access to the vehicle.
This might seem far-fetched but there have been such incidences in the past that corroborate such claims. Moreover, some researchers have performed such cyber-attacks on infotainment and other systems to bring out their vulnerability to cyber-attacks.
However, automotive OEMs and other entities in the automotive value-chain do realize these threats. The introduction of a cybersecurity standard ISO-SAE DIS 21434 is also helping in making cybersecurity a part of the software and hardware development lifecycle.
We will learn about all these aspects in the subsequent sections of the blog. Read on..
Why is Automotive Cybersecurity Such a Big Deal?
Automobiles have transitioned from being wheels driven by an engine to a sort of data center on wheels. A modern-day car with some advanced features can have 150 ECUs with more than 100 million lines of source code. The cyber risk to a modern vehicle increases with every line of code burnt on the automotive ECUs. Hence, each line of code must conform to the measures stipulated in the cybersecurity standards.
Moreover, the threat is not just limited to the vehicle itself but also transcends to the back-end and 3rd party services. A good example of an attack on such services is controlling a home EV charging installation by accessing the home Wi-Fi.
When we bring connected and autonomous vehicles into the picture, the threat can take a more hazardous form.
We have summarized some findings from last year’s cyber-attack incidences:
- An SUV was hacked by a few white hat hackers to control the climate control feature, infotainment system and even steering and braking system. Fortunately, this hack was part of a research done by some cyber-security experts.
- The percentage of black hat hacking incidences (hacking done with malicious intentions) had risen to 72% in the first few months of 2019.
- Keyless remote entry, a popular feature in vehicles, has been the preferred vector for cyber-attacks.
- A parking garage meant for employees of a Canadian organization was attacked by a ransomware that allowed free parking and even without verification of the access cards. This attack was a classic case of attack on back-end systems meant to facilitate automobile users.
- In an incident of attack on an alarm system server, the hackers were able to track the vehicles, unlock their doors and even cut off their engines in some cases.
Every new feature or functionality added to a vehicle system adds to the risk of cyber-attack. In order to mitigate them, we must first understand the threats and where they emanate from. Let’s learn a bit about that too!
Automotive Innovations and Cybersecurity: Understanding the Threat
Automotive industry has been innovating at an unprecedented pace and most of it is driven by software. And we have already discussed how each line of code in the software increases the vulnerability. According to Mckinsey reports, the software and E/E component market is expected to grow from USD 238 billion in 2020 to USD 469 billion over the next 10 years. Let’s understand the cyber threat that emanates from these innovations:
- Connected Cars: Automobiles are evolving rapidly into connected devices equipped with Bluetooth and Wi-Fi based communication. Technologies like vehicle to infrastructure, vehicle to vehicle, vehicle to cloud, and vehicle to everything make the car vulnerable to cyber-attacks. Once, the hackers get access to the vehicle to cloud network, they can potentially hack the entire fleet of vehicles connected to that cloud network.
- Highly Autonomous Vehicles: Autonomous vehicles once seemed like fables straight from a fiction novel or a sci-fi movie. Fast forward to 2020, OEMs have driven the autonomous vehicles millions of miles on the roads. These vehicles rely not only on the sensors fitted in the car, but also a stream of data from the infrastructure around them including GPS and traffic data. Any breach in the system can lead to fatal accidents.
- Electric Vehicles: The cybersecurity aspect of an EV is no different than an IC engine vehicle. However, an added vulnerability in the form of Electric vehicle charging station is added when cybersecurity is discussed in the context of electric vehicles. A cyber-attack on the charging infrastructure can lead to serious consequences like fire and power issues.
Source: Joelynn Schroeder, NREL
Vehicle Cybersecurity Across Value-Chain
Different components of a vehicle are developed by multiple entities viz, OEM, Tier-1 supplier, After-market vendors, Technology solution providers and others. These components need to be developed keeping in mind the cybersecurity aspect. Hence, the approach has to be uniform across the automotive value-chain.
Following are some of the stakeholders and their role in ensuring automotive cyber-security:
- Original Equipment Manufacturer: OEMs are responsible for crafting a vehicle with its trademark characteristics. In this process, the OEM procures different components from Tier-1 and After-market suppliers. Hence, it is the role of the OEM to define clear guidelines on the cybersecurity aspects to follow. While sourcing technology from other vendors, they have to make sure that they follow these guidelines across the development process. Compliance with cyber-security standard ISO/SAE DIS 21434 can act as a good reference point for this activity. The OEM must ask for work-products (evidences) of their compliance with the standard.
- Tier-1 Supplier: Tier-1 suppliers must be aware of the cyber risks involved in the component that they are providing to the OEMs. For instance, an Android-based infotainment system provided by a supplier must conform to development keeping cyber-risks under consideration, both at the software and hardware levels.
- Technology Service Provider: Tier-1 suppliers often outsource technology solutions development to product engineering service providers. These vendors provide design and development support including reference designs, prototype development, automotive protocol stacks configuration and integration, testing services and more. Similar to the Tier-1 suppliers, the technology partners should also be in sync with cyber-security requirements that have been defined at the top of the pyramid, i.e. by the OEMs.
Understanding the Types of Cyber-attacks on Vehicles
Over the years, cyber-attacks have evolved and so have their prevention methods. However, in order to keep vehicles safe from these threats, it’s imperative that cybersecurity measures are always in place. And to ensure that, we must first understand the kind of threats that can affect a vehicle.
Denial of Service (DOS): It is an attack that overwhelms an automotive system to make it unresponsive to requests. For example, a DOS attack on the ABS ECU can disable the braking system of the vehicle. A DOS attack does not give the hacker access to the system, but it can surely be used for malicious intentions such as injuring a vehicle occupant.
Man-in-the-middle (MitM) attack: When a hacker inserts himself between the client and the server, it is called a MitM attack. In such an attack, the attacker can spoof the client and steal data from the server.
Command injection data corruption: By injecting a specialized command, the attackers can gain a write access to an ECU and corrupt the data stored in the ECU. Depending on how critical the ECU is, such attacks can wreak havoc on a vehicle system.
There are many such types of attacks possible. Once the attackers are aware of the vulnerability, they can choose the mode of attack.
Best Practices to Achieve Vehicle Cybersecurity
As mentioned earlier, cybersecurity measures must be followed across the development lifecycle (security by design) of an automotive component. On top of that, there are certain best practices that aid in achieving cybersecurity in the entire automotive ecosystem. Let’s discuss a few of them.
- Interfaces to the outside world should be secure. These interfaces include over-the-air update (OTA), OBD, Bluetooth and Ethernet.
- ECUs that are safety-related should be isolated and protected using secure gateways.
- Apart from software related measures, Hardware Security Module (HSM) must be implemented for Microcontroller platforms. HSM plays a key role in delivery of security services like Trusted Execution Environment (TEE) for the applications.
- Automotive cybersecurity guidelines as mandated by ISO 21434 must be followed by all stakeholders across the automotive supply-chain.
- Protocol stacks such as UDS, DoIP, SOME/IP, FlexRay must be developed as per the cybersecurity guidelines and must have built-in security firewalls.
- Hardening of the ECUs by deleting all the interfaces and services that can be potential entry-points for the attackers is a must.
- Cybersecurity guidelines should be followed during unit testing, integration testing and system testing of hardware and software modules.
A Brief Overview of ISO/SAE DIS 21434
Discussion on automotive cybersecurity is incomplete without the mention of ISO/SAE DIS 21434 standard. Similar to ISO 26262 in structure and scope, this standard covers the cybersecurity engineering aspects for road vehicles.
The standard was first published in the year 2016 by the joint effort of ISO and SAE. The aim of this standard is to provide guidelines on how to manage automotive cybersecurity, similar to how ISO 26262 standard manages the Functional Safety for road vehicles.
A Snapshot of ISO/SAE DIS 21434 standard:
- Cybersecurity Management: This deals with the goals and objectives of cybersecurity management such as defining the objectives, strategies, establishing a cybersecurity culture and so on.
- Methods for Risk Assessment: This part showcases the methods to assess the risks associated with assets. Vulnerability and attack analysis is performed at this stage.
- Concept Phase: At this stage, the exposure to cybersecurity risk is determined for a specific automotive component. Goals are defined to reduce the risks.
- Product Development: This is a reference for cybersecurity guidelines to be followed during system, software and hardware design.
- Supporting Processes: This section enlists the management systems to support the activities undertaken to achieve cybersecurity. Cybersecurity Assurance Level (CAL) classification scheme is introduced here. It is essentially a measure of how rigorous cybersecurity requirements should be for a particular item. It is similar to ASIL in ISO 26262.
Final Thoughts
Cybersecurity is now a priority for automotive OEMs and other stakeholders, and rightly so. It is also seen as one of the quality aspects of a vehicle, given the fact that automobiles are more connected than they ever were. It will be interesting to see how the industry addresses the pain points related to cybersecurity in the coming years.


